Konfiguracja klienta VPN - Router Mikrotk

Zaloguj się do swojego routera, uruchom przeglądarkę lub skorzystaj z aplikacji WINBOX.
Wpisz domyślny adres routera: http://192.168.88.1
Przejdź do zakładki "PPP" (1) i dodaj (2) nowy interface "PPTP Client" (3)
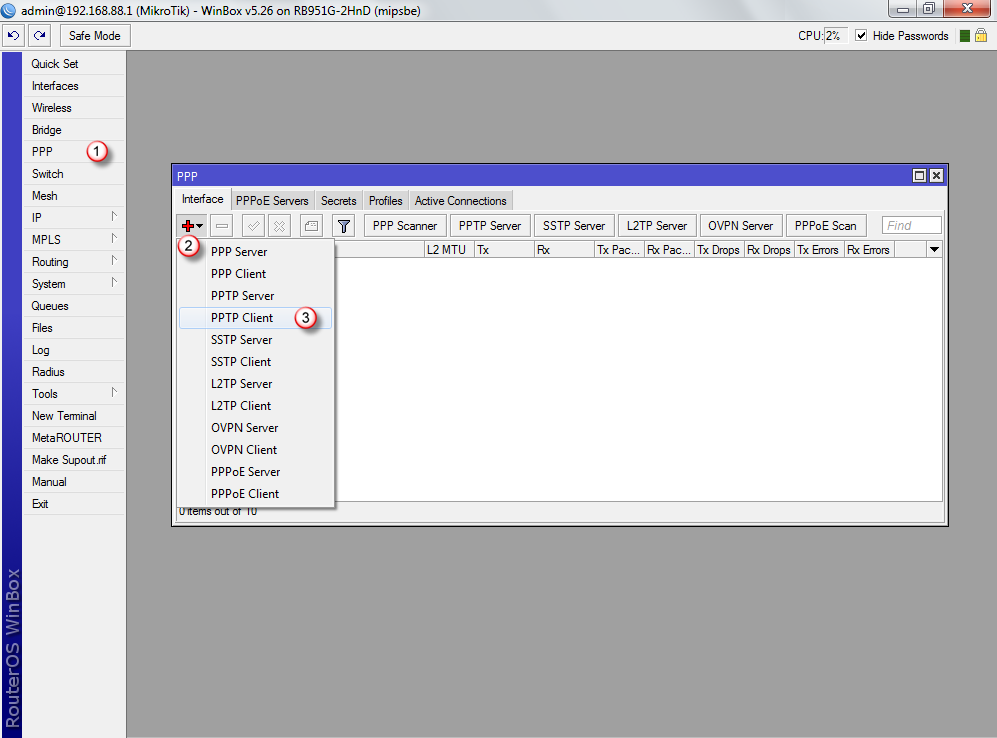
W zakładce "General" (4), w polu "Name" (5) wpisz nazwę interfajsu: VPNonline-PPTP
W polu "Max MTU" (6) oraz "Max MRU" (7) wpisz wartość: "1400"
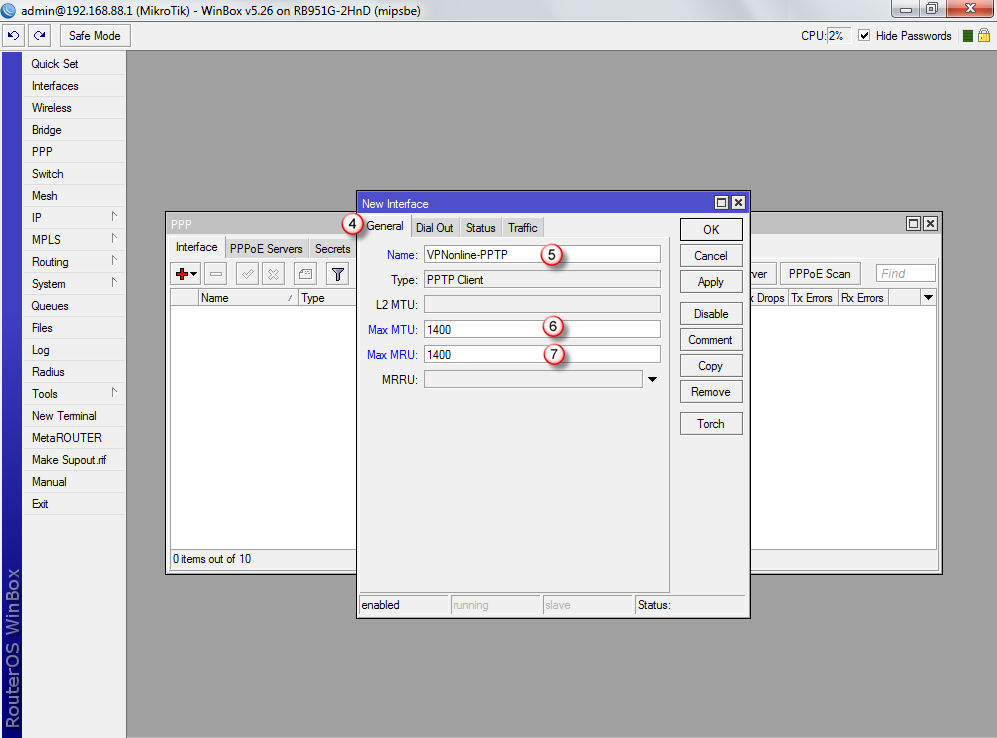
Kliknij zakładkę "Dial Out" (8) i wypełnij poniższe pola:
W polu "Connect to:" (9) wpisz nazwę jednego z naszych serwerów VPN
Listę dostępnych serwerów VPN znajdziesz w panelu klienta: https://portal.vpnonline.pl
W polu "User:" (10) wpisz swój login
W polu "Password:" (11) wpisz swoje hasło
Aby zatwierdzić wprowadzone dane, kliknij "OK" (12)
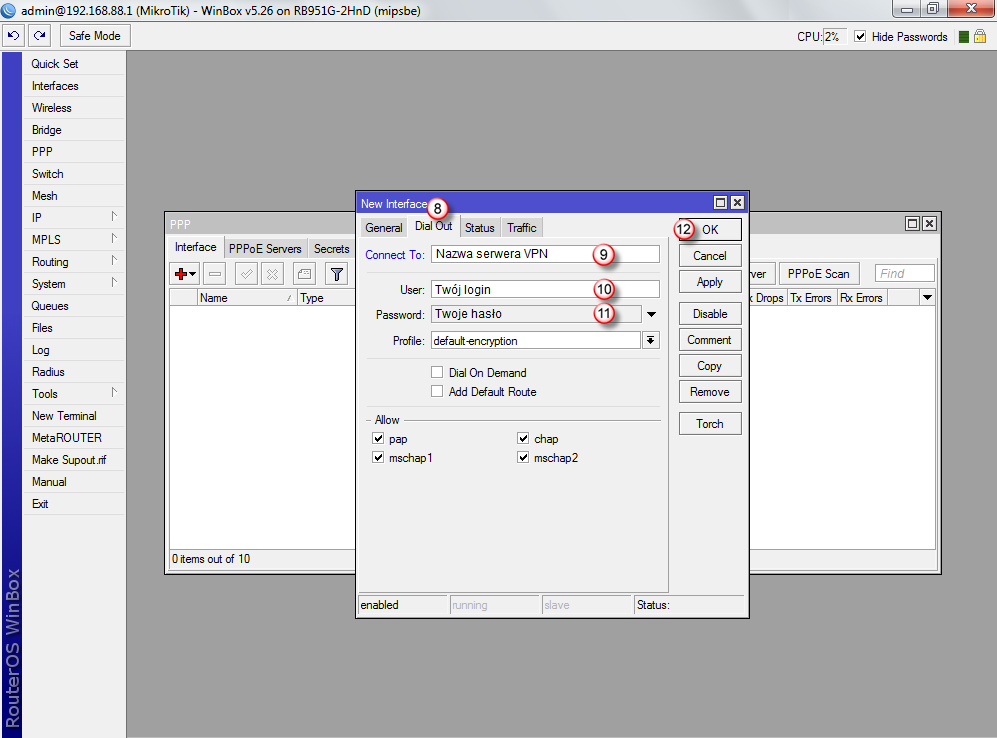
Kliknij zakładkę "IP" (13) i następnie "Firewall" (14)
W oknie "Firewall" wybierz zakładkę "NAT" (15), następnie dodaj nową regułę (16)
W zakładce "General" (17) wybierz "Chain: srcnat" (18) i następnie "Out. Interface: VPNonline-PPTP" (19)
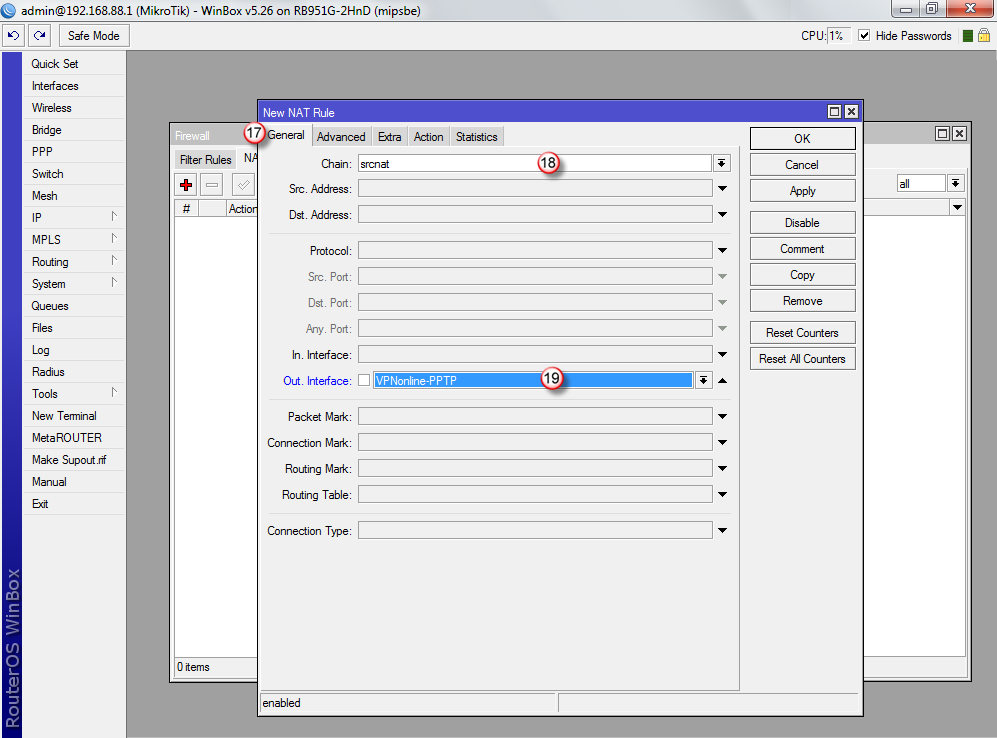
Następnie przejdź do zakładki "Action" (20) i w polu "Action" (21) wybierz "masquerade".
Kliknij "OK" (22)
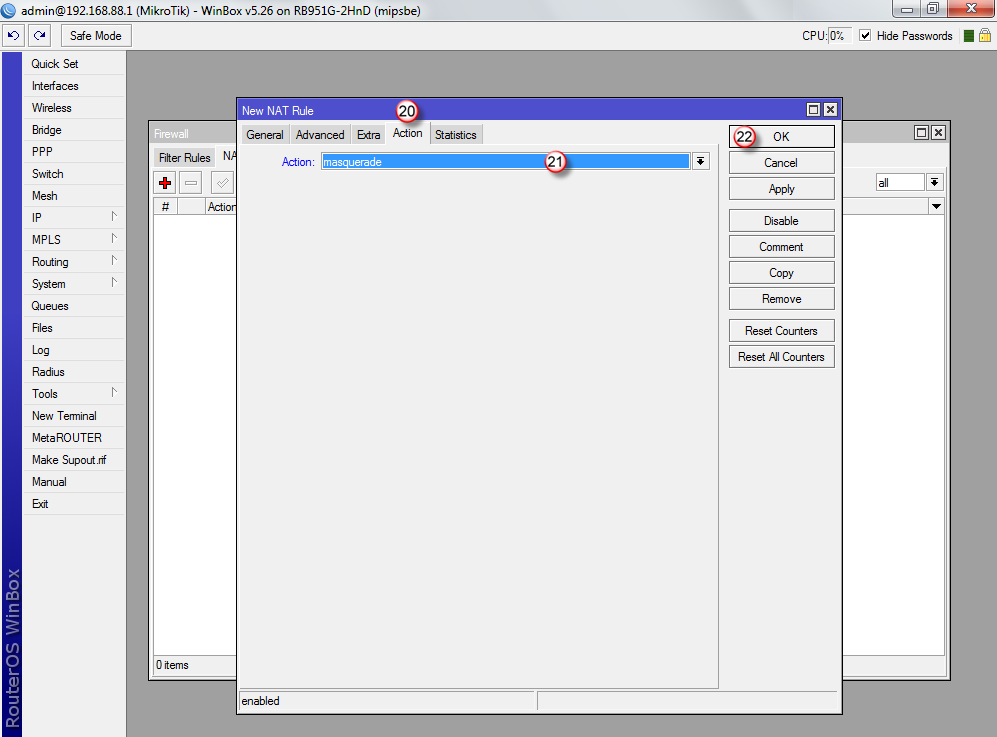
Przejdź do zakładki "Mangle" (23) i dodaj nową regułę (24)
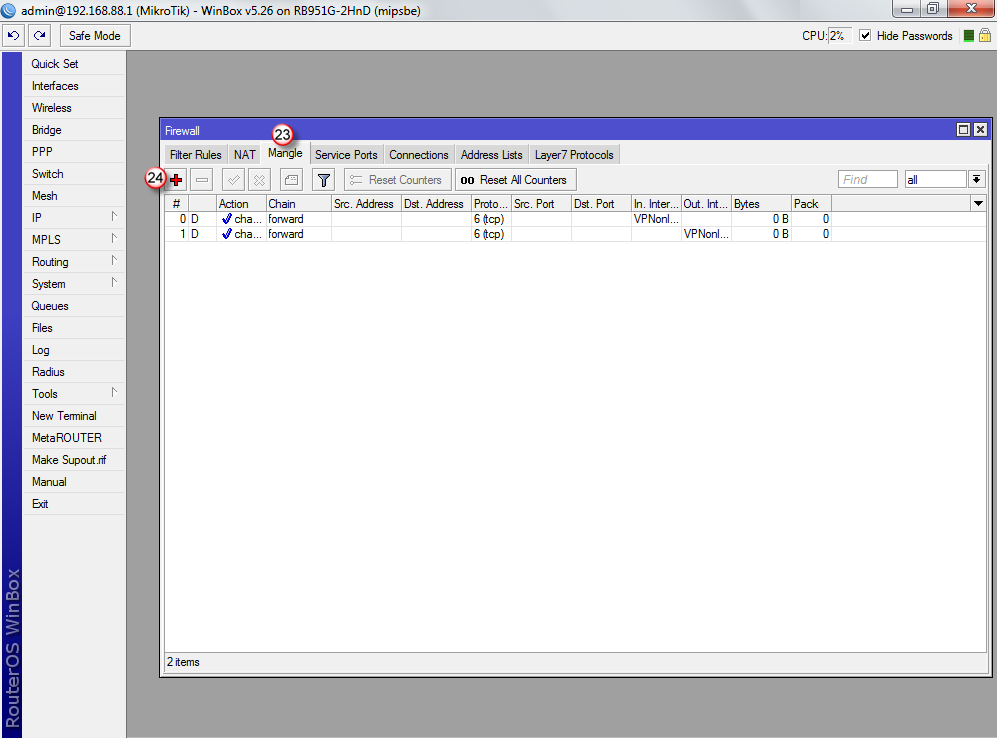
W oknie "New Mangle Rule", wybierz zakładkę "General" (25), następnie wybierz "Chain: prerouting" (26) oraz w polu "Src Address" (27) wpisz adresy IP komputerów, które mają przechodzić przez tunel VPN.
W przykładzie, wpisana jest całą pula adresów IP 192.168.88.2 - 192.168.88.254, ale możesz wpisać tu pojedynczy adres IP hosta np. 192.168.88.10. Dzięki temu, tylko ten host będzie przechodził przez VPN i tylko jego publiczny adres IP zmieni się na adres IP serwera VPN (np. Polski). Pozostałe hosty z puli 192.168.88.0 będą wychodzić przez lokalne łącze do Internetu i będą widoczne w Internecie pod lokalnym publicznym adresem IP.
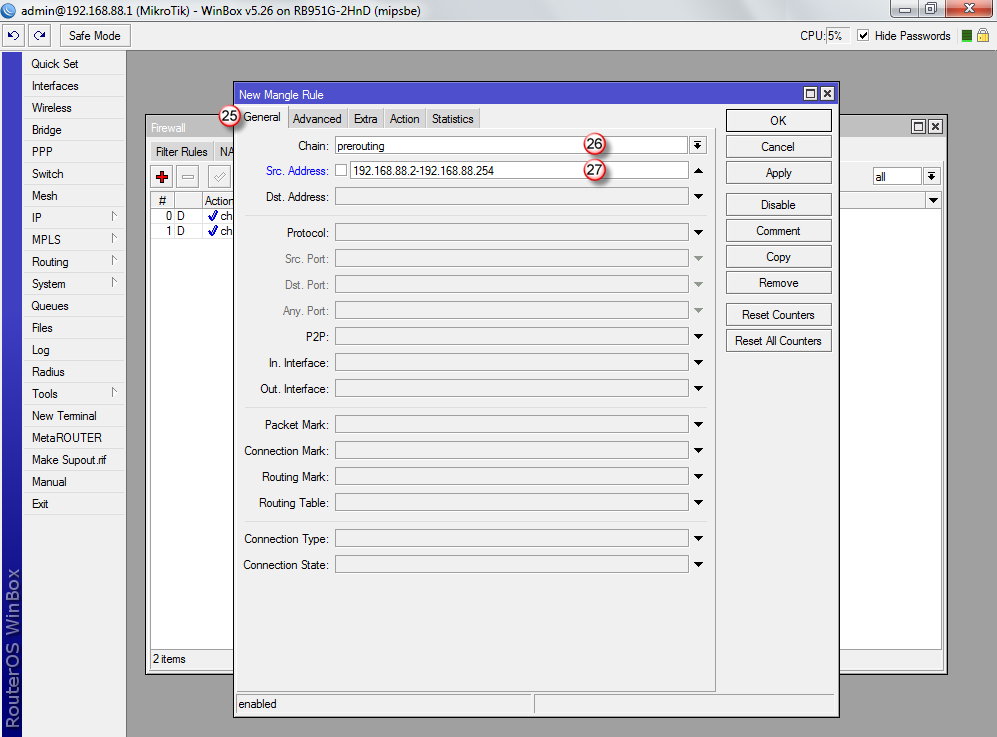
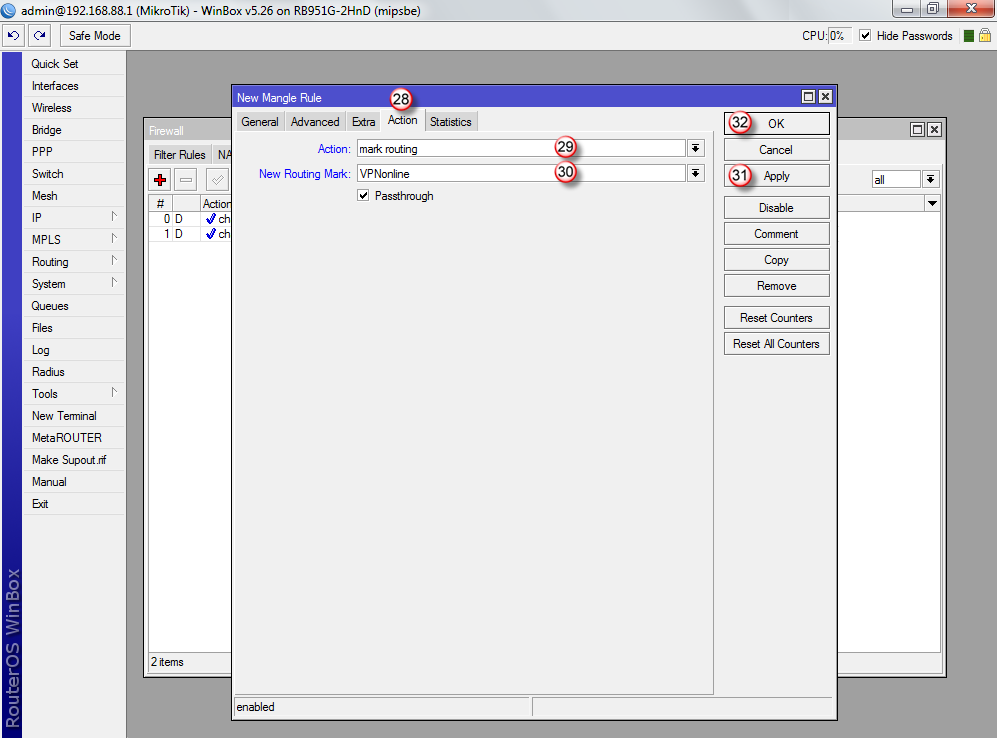
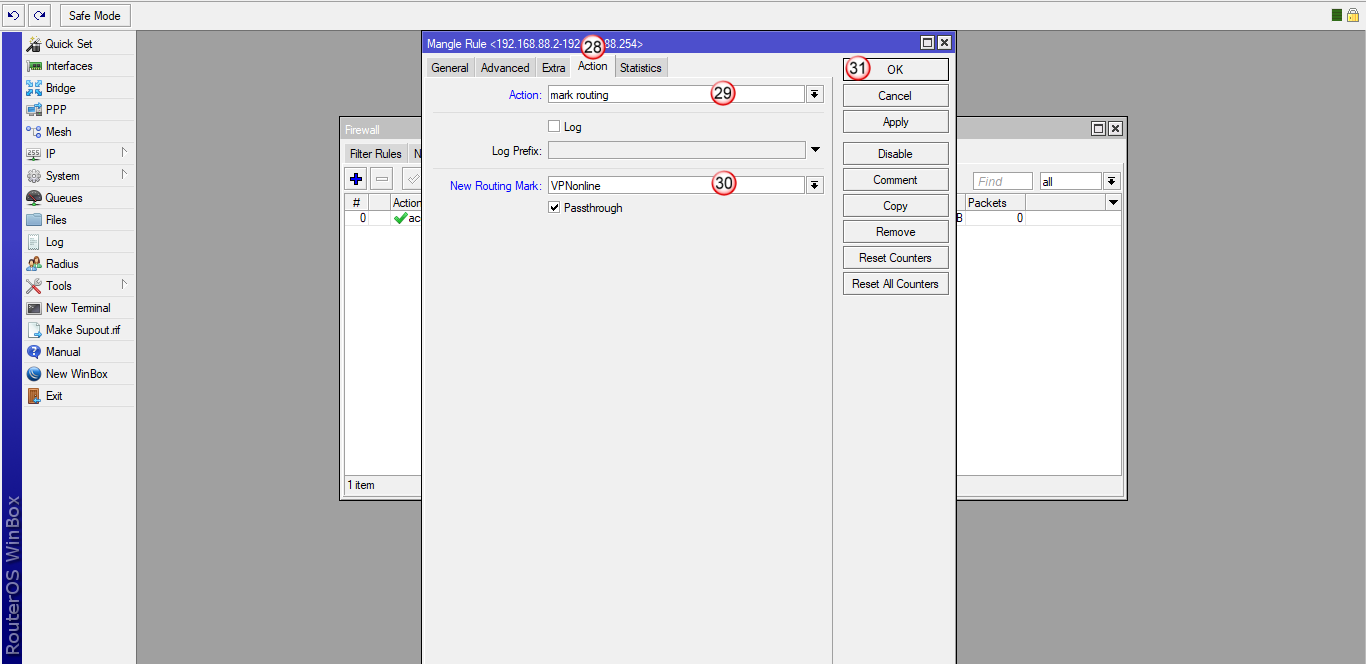
Przejdź do zakładki "Action" (28), w polu "Action" wybierz "mark routing" (29)
W polu "New Routing Mark" (30) wpisz "VPNonline"
Aby zatwierdzić zmiany, kliknij "Apply: (31) i następnie "OK" (32)
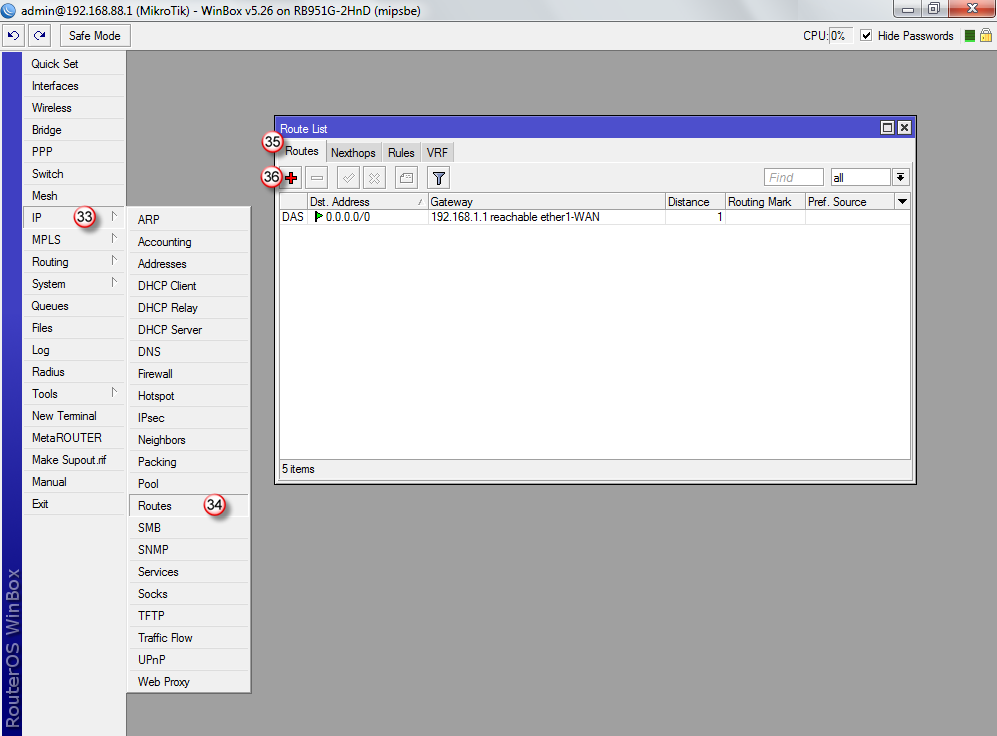
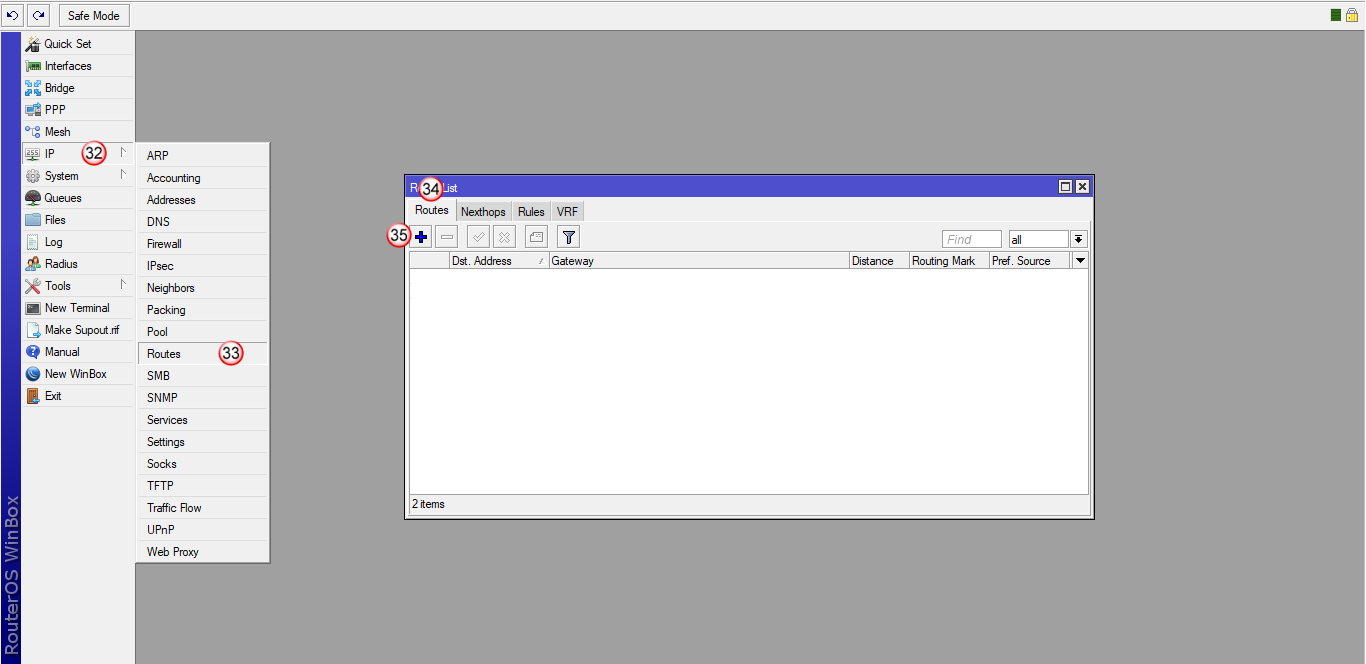
Przejdź do zakładki "IP" (33) i "Routes" (34)
W oknie "Route List", w zakładce "Routes" (35), dodaj nową regułę (36)
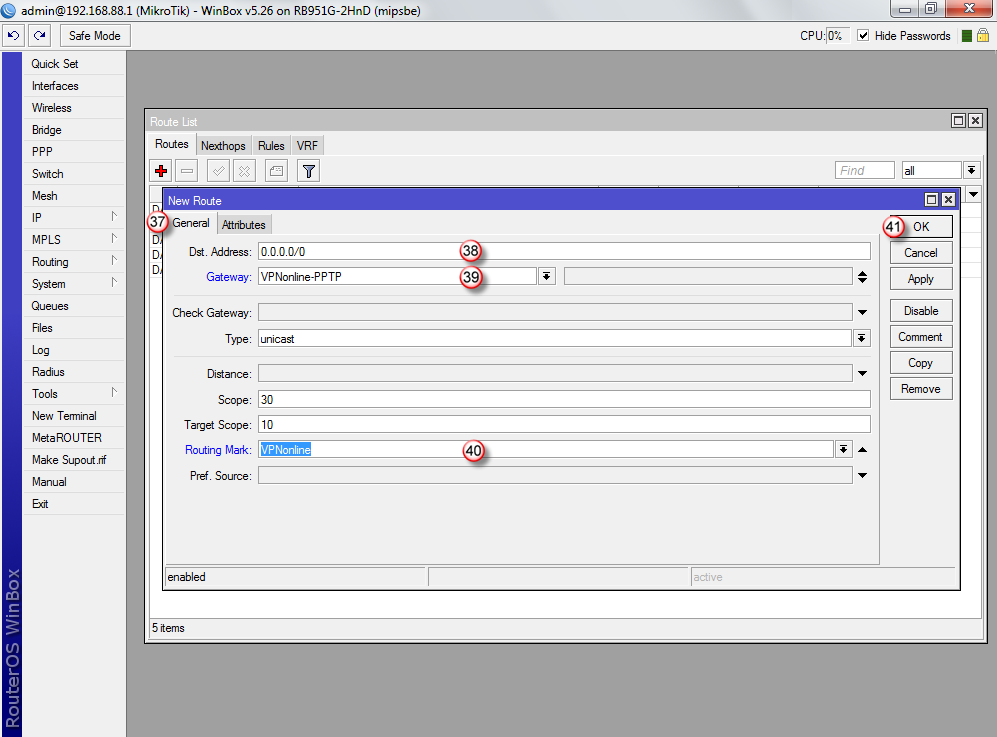
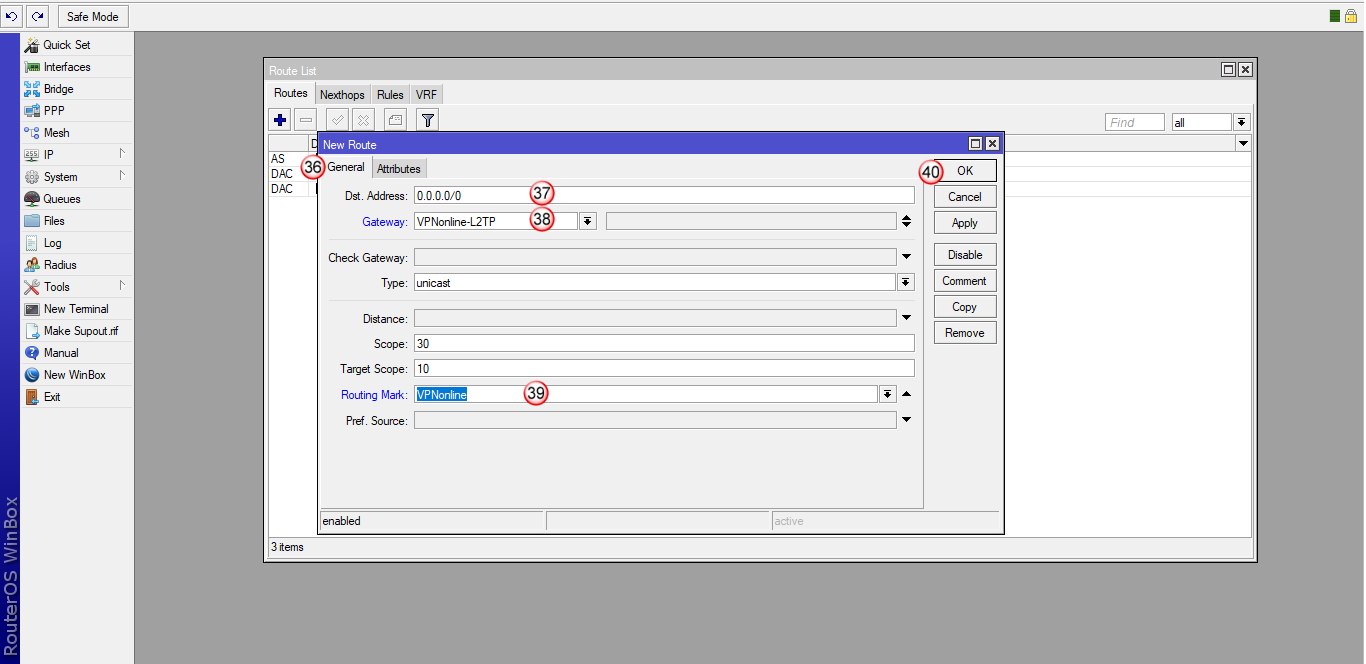
W oknie "New Route", w zakładce "General" (37) wybierz:
"Dst. Address" (38) - 0.0.0.0/0
"Gateway" (39) - VPNonline-PPTP
"Routing Mark" (40) - VPNonline
Aby zatwierdzić zmiany, kliknij "OK" (41)
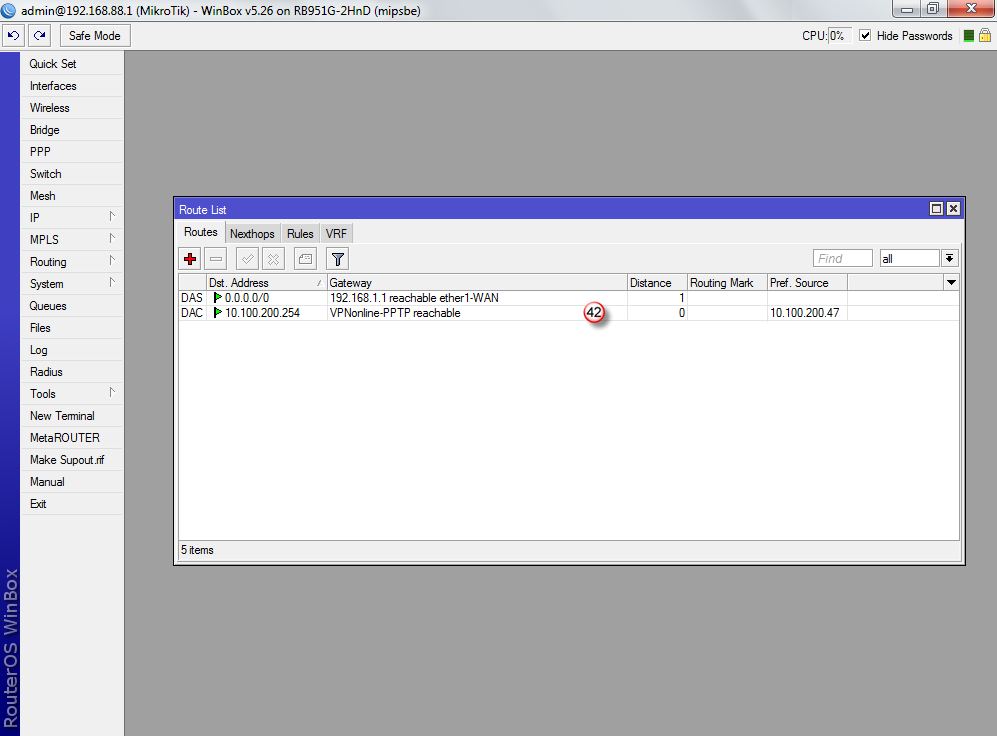
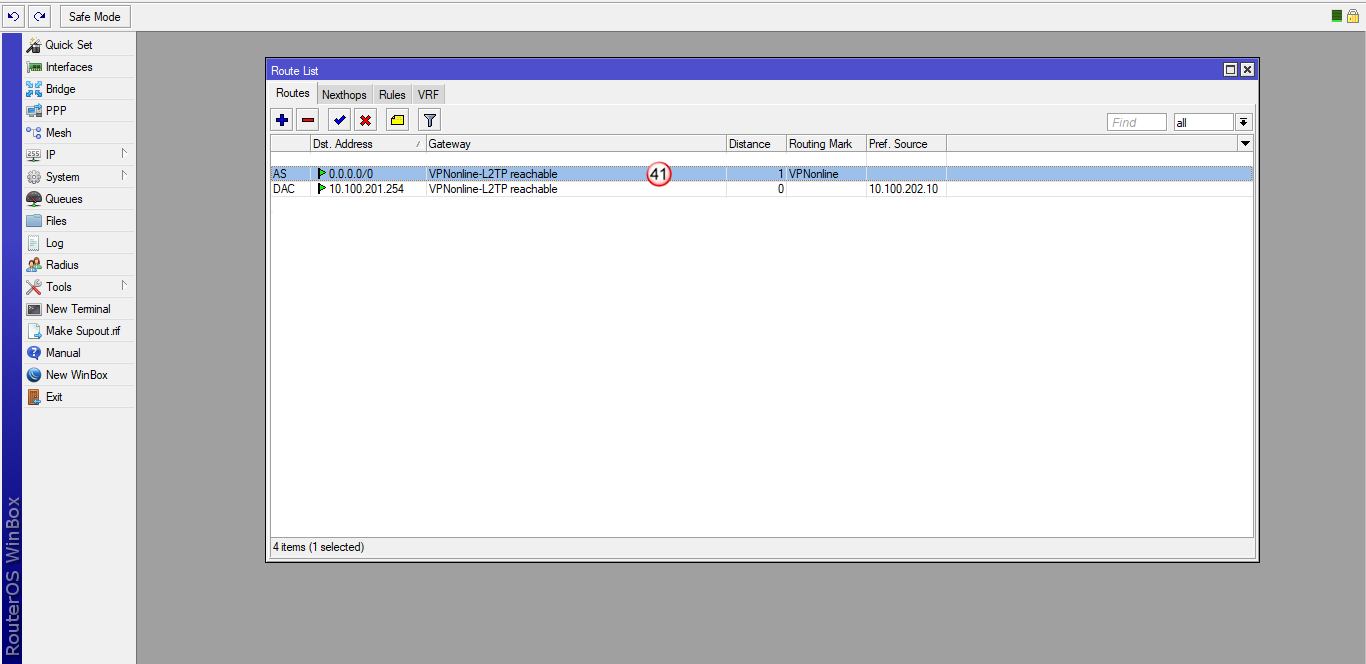
Nowa trasa routingu została dodana (42) i połączenie VPN powinno się zestawić.
Zaloguj się do swojego routera, uruchom przeglądarkę lub skorzystaj z aplikacji WINBOX.
Wpisz domyślny adres routera: http://192.168.88.1
Przejdź do zakładki "PPP" (1) i dodaj (2) nowy interface "L2TP Client" (3)
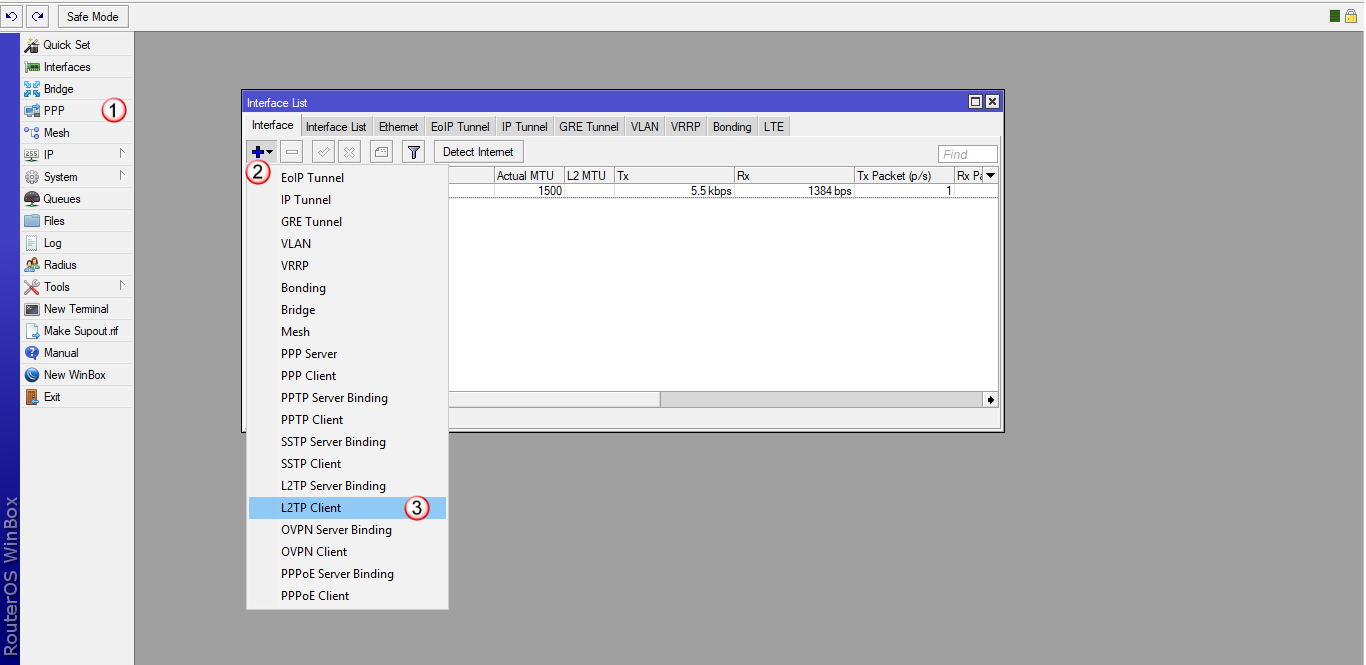
W zakładce "General" (4), w polu "Name" (5) wpisz nazwę interfajsu: VPNonline-L2TP
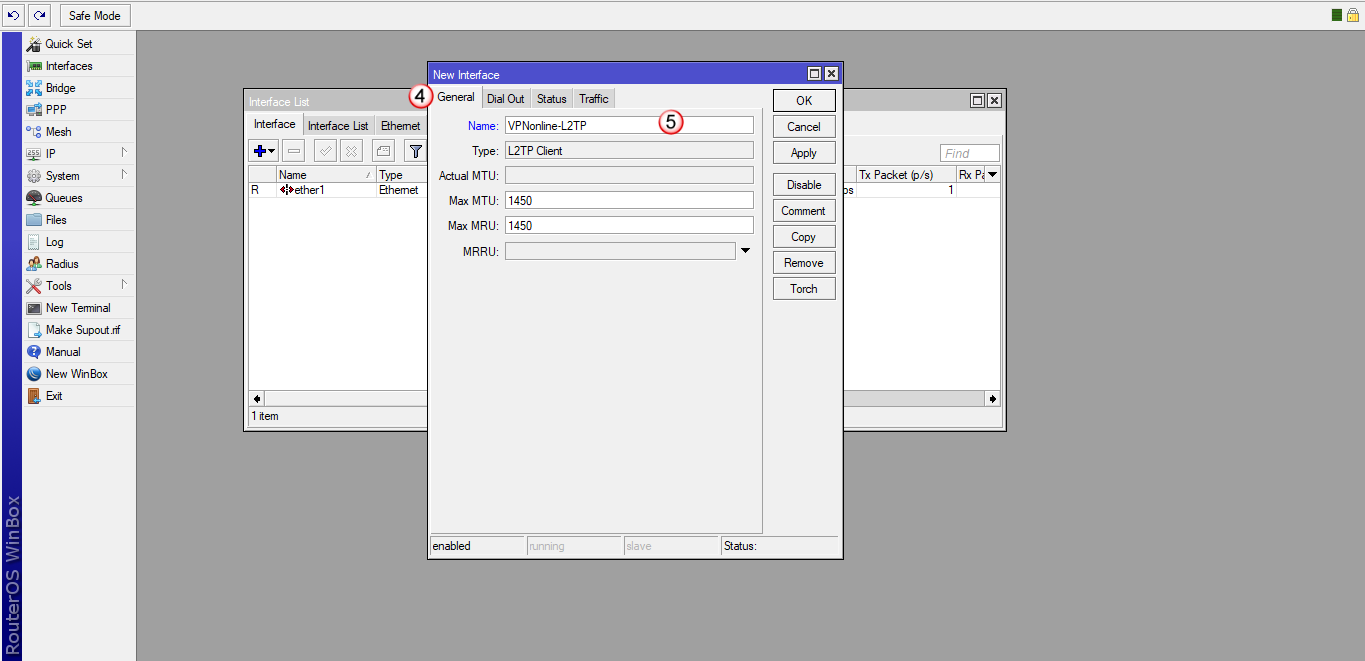
Kliknij zakładkę "Dial Out" (6) i wypełnij poniższe pola:
W polu "Connect to:" (7) wpisz nazwę jednego z naszych serwerów VPN
Listę dostępnych serwerów VPN znajdziesz w panelu klienta: https://portal.vpnonline.pl
W polu "User:" (8) wpisz swój login
W polu "Password:" (9) wpisz swoje hasło
Zaznacz "Use IPsec" i w polu "IPsec Secret:" (10) wpisz: vpnonline.pl
Zaznacz "Allow mschap2" (11)
Aby zatwierdzić wprowadzone dane, kliknij "OK" (12)
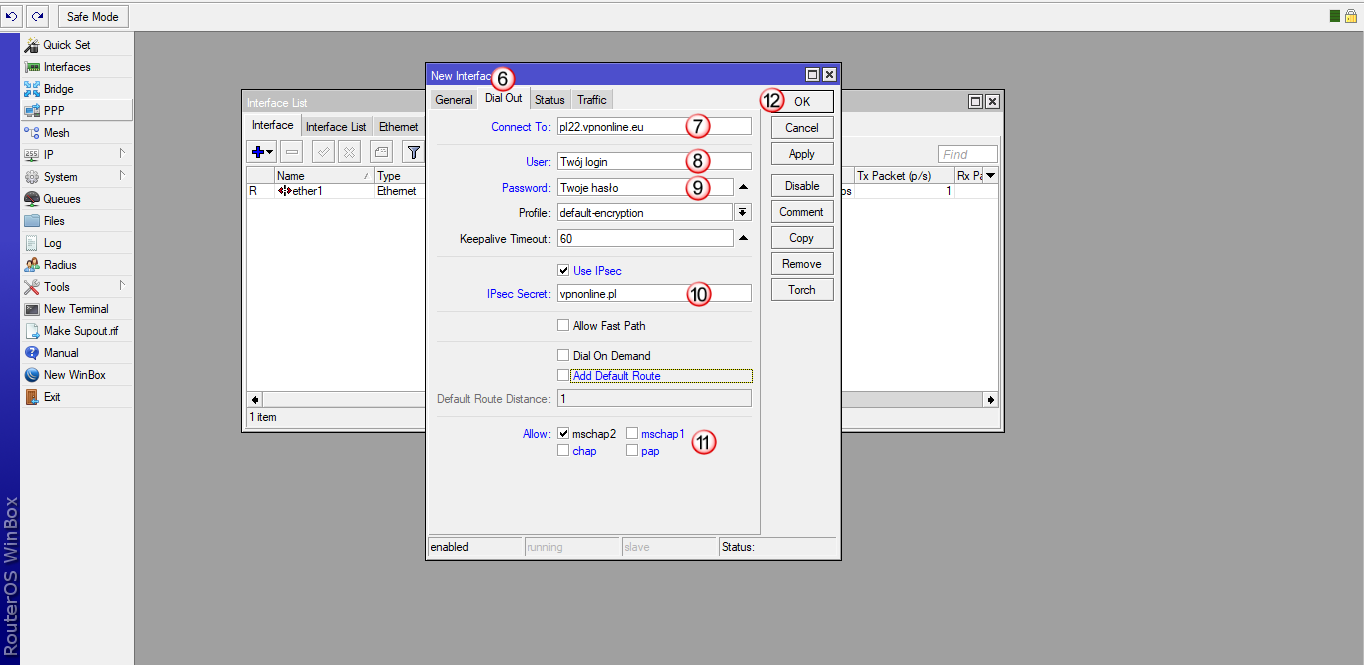
Kliknij zakładkę "IP" (13) i następnie "Firewall" (14)
W oknie "Firewall" wybierz zakładkę "NAT" (15), następnie dodaj nową regułę (16)
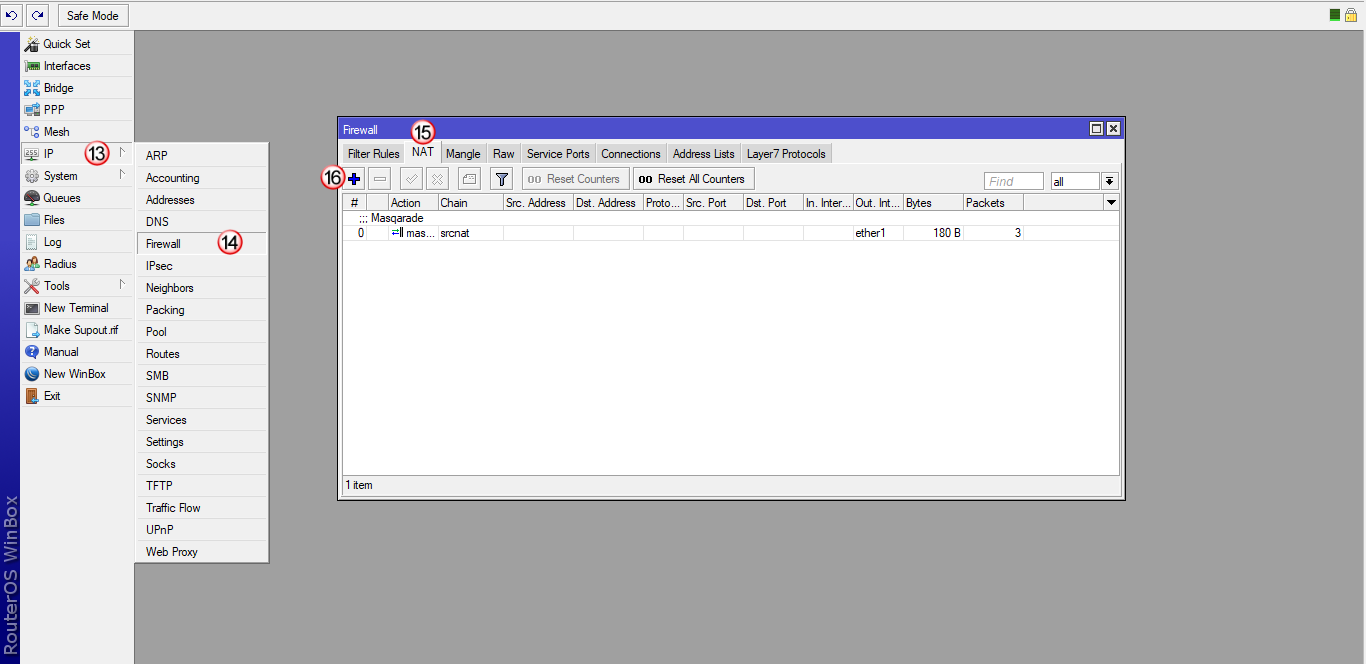
W zakładce "General" (17) wybierz "Chain: srcnat" (18) i następnie "Out. Interface: VPNonline-L2TP" (19)
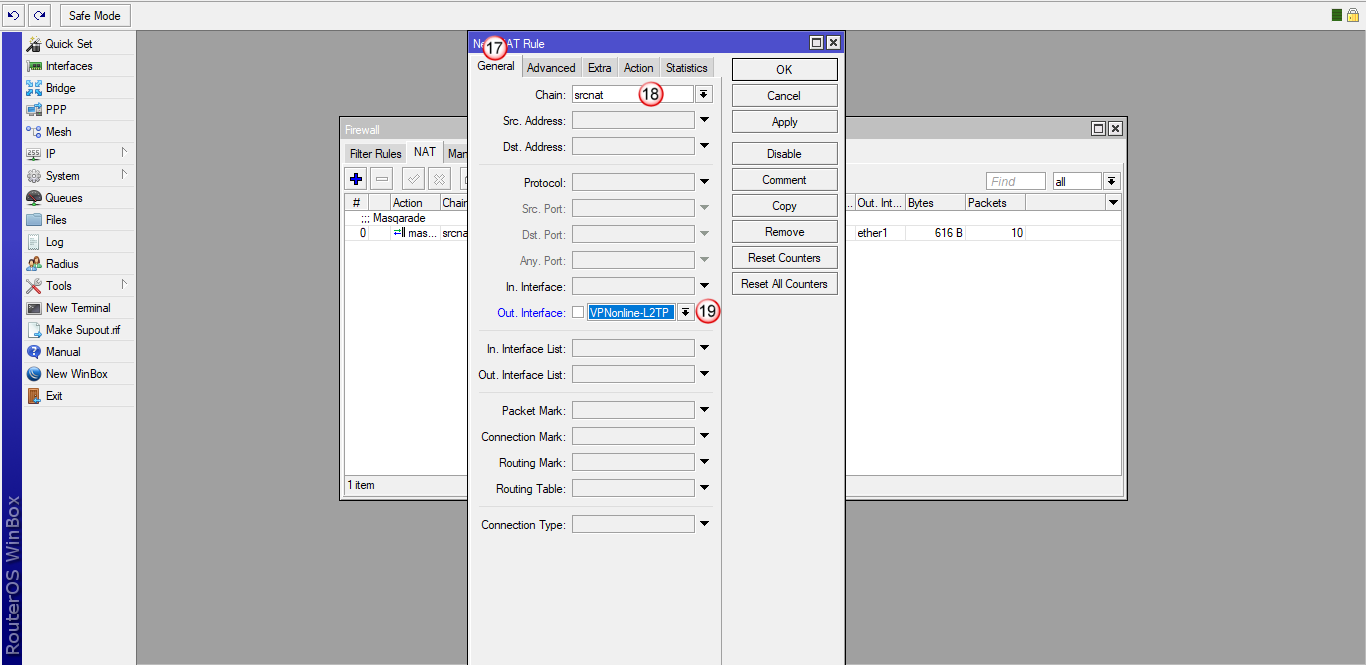
Następnie przejdź do zakładki "Action" (20) i w polu "Action" (21) wybierz "masquerade".
Kliknij "OK" (22)
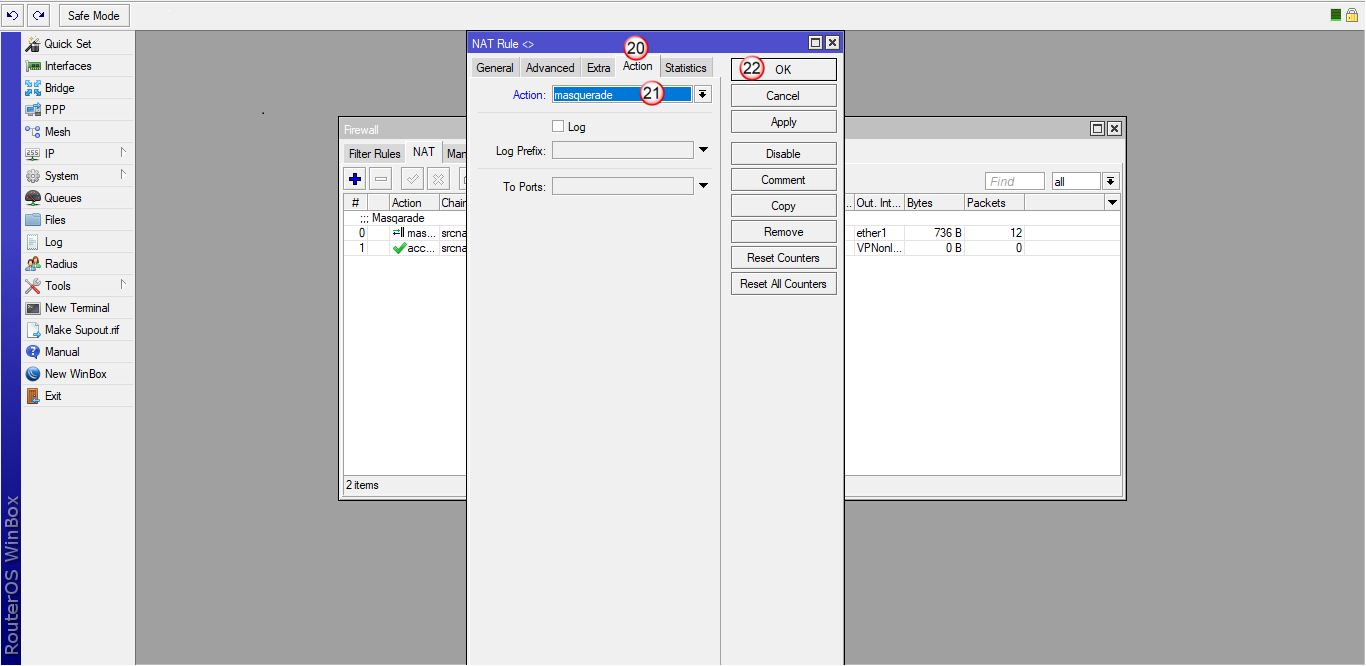
Przejdź do zakładki "Mangle" (23) i dodaj nową regułę (24)
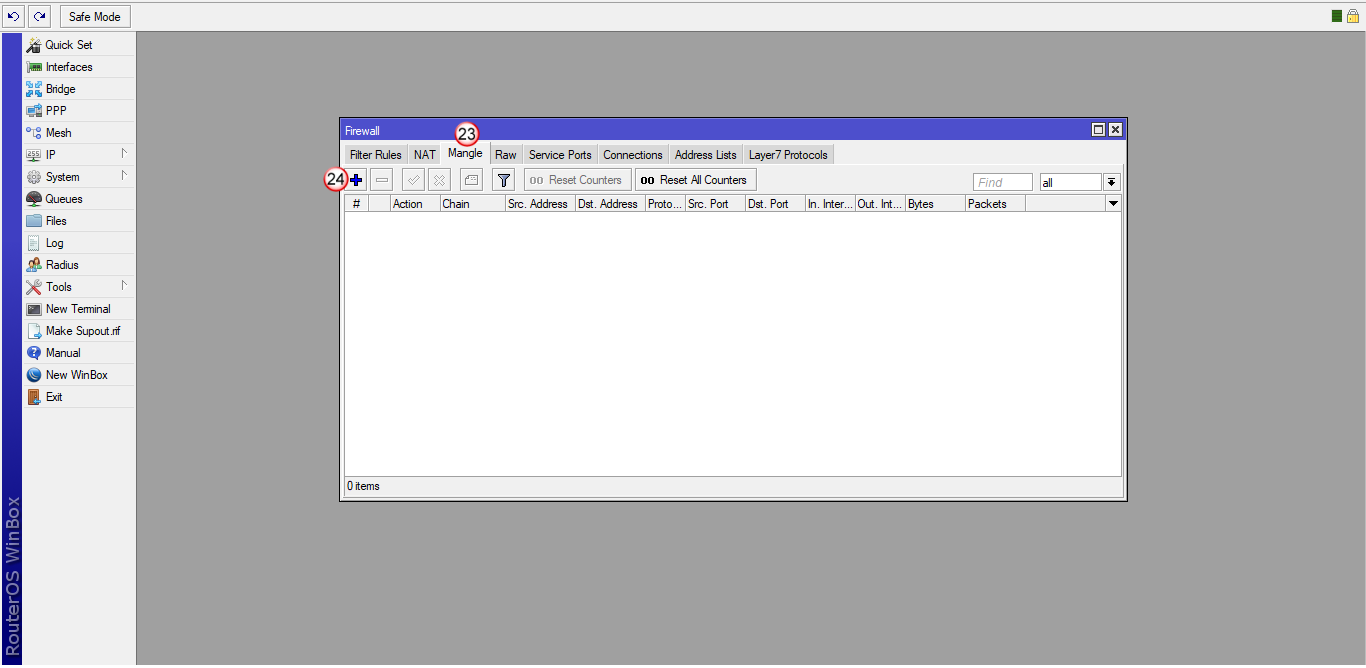
W oknie "New Mangle Rule", wybierz zakładkę "General" (25), następnie wybierz "Chain: prerouting" (26) oraz w polu "Src Address" (27) wpisz adresy IP komputerów, które mają przechodzić przez tunel VPN.
W przykładzie, wpisana jest całą pula adresów IP 192.168.88.2 - 192.168.88.254, ale możesz wpisać tu pojedynczy adres IP hosta np. 192.168.88.10. Dzięki temu, tylko ten host będzie przechodził przez VPN i tylko jego publiczny adres IP zmieni się na adres IP serwera VPN (np. Polski). Pozostałe hosty z puli 192.168.88.0 będą wychodzić przez lokalne łącze do Internetu i będą widoczne w Internecie pod lokalnym publicznym adresem IP.
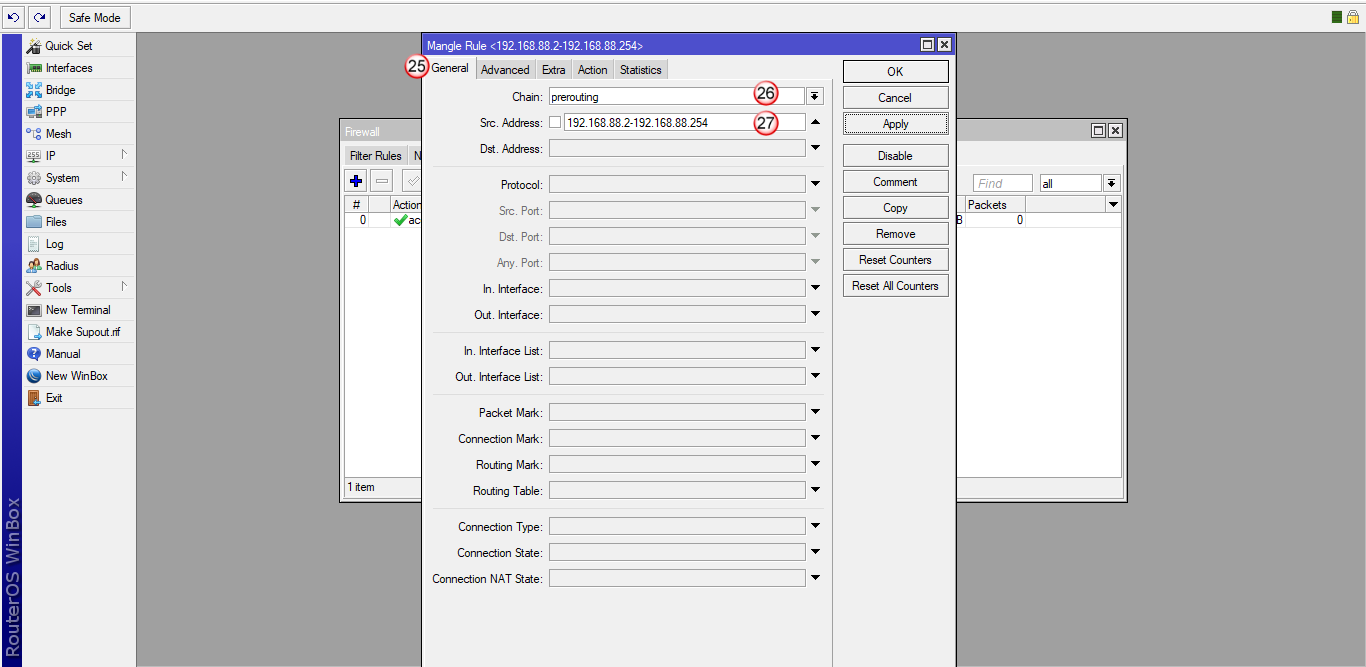
Przejdź do zakładki "Action" (28), w polu "Action" wybierz "mark routing" (29)
W polu "New Routing Mark" (30) wpisz "VPNonline"
Aby zatwierdzić zmiany, kliknij "OK" (31)
Przejdź do zakładki "IP" (32) i "Routes" (33)
W oknie "Route List", w zakładce "Routes" (34), dodaj nową regułę (35)
W oknie "New Route", w zakładce "General" (36) wybierz:
"Dst. Address" (37) - 0.0.0.0/0
"Gateway" (38) - VPNonline-L2TP
"Routing Mark" (39) - VPNonline
Aby zatwierdzić zmiany, kliknij "OK" (40)
Nowa trasa routingu została dodana (41) i połączenie VPN powinno się zestawić.
Zaloguj się do swojego routera, uruchom przeglądarkę lub skorzystaj z aplikacji WINBOX.
Wpisz domyślny adres routera: http://192.168.88.1
Przejdź do zakładki "PPP" (1) i dodaj (2) nowy interface "SSTP Client" (3)
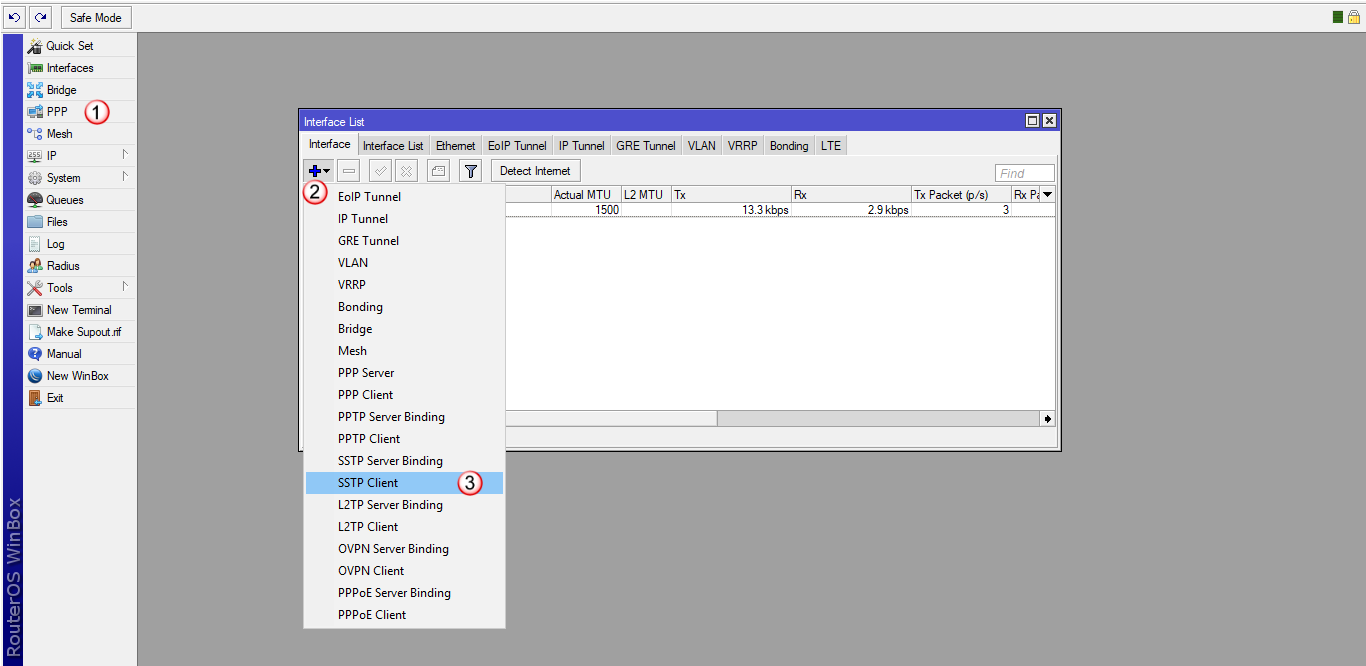
W zakładce "General" (4), w polu "Name" (5) wpisz nazwę interfajsu: VPNonline-SSTP
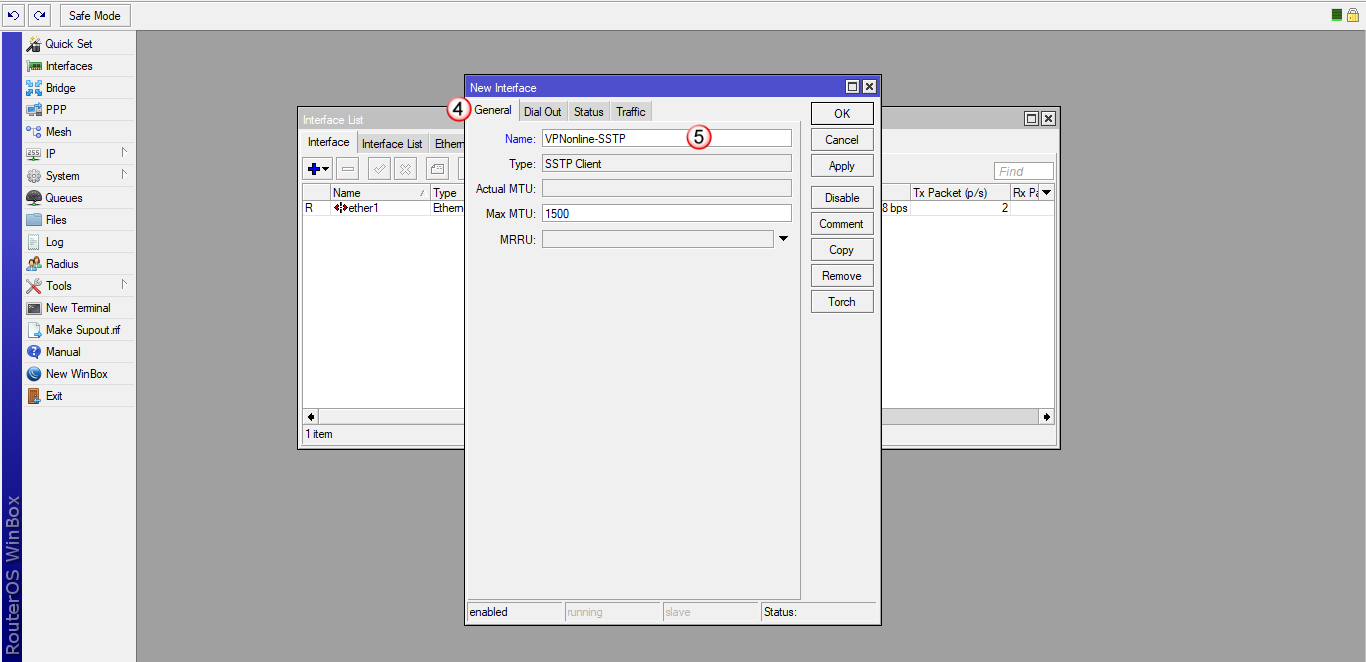
Kliknij zakładkę "Dial Out" (6) i wypełnij poniższe pola:
W polu "Connect to:" (7) wpisz nazwę jednego z naszych serwerów VPN
Listę dostępnych serwerów VPN znajdziesz w panelu klienta: https://portal.vpnonline.pl
W polu "Port:" (8) wpisz: "443"
Odznacz: "Verify Server Certificate" oraz pozostałe (9)
W polu "User:" (10) wpisz swój login
W polu "Password:" (11) wpisz swoje hasło
W polu "Allow:" (12) zaznacz tylko "mschap2"
Aby zatwierdzić wprowadzone dane, kliknij "OK" (13)
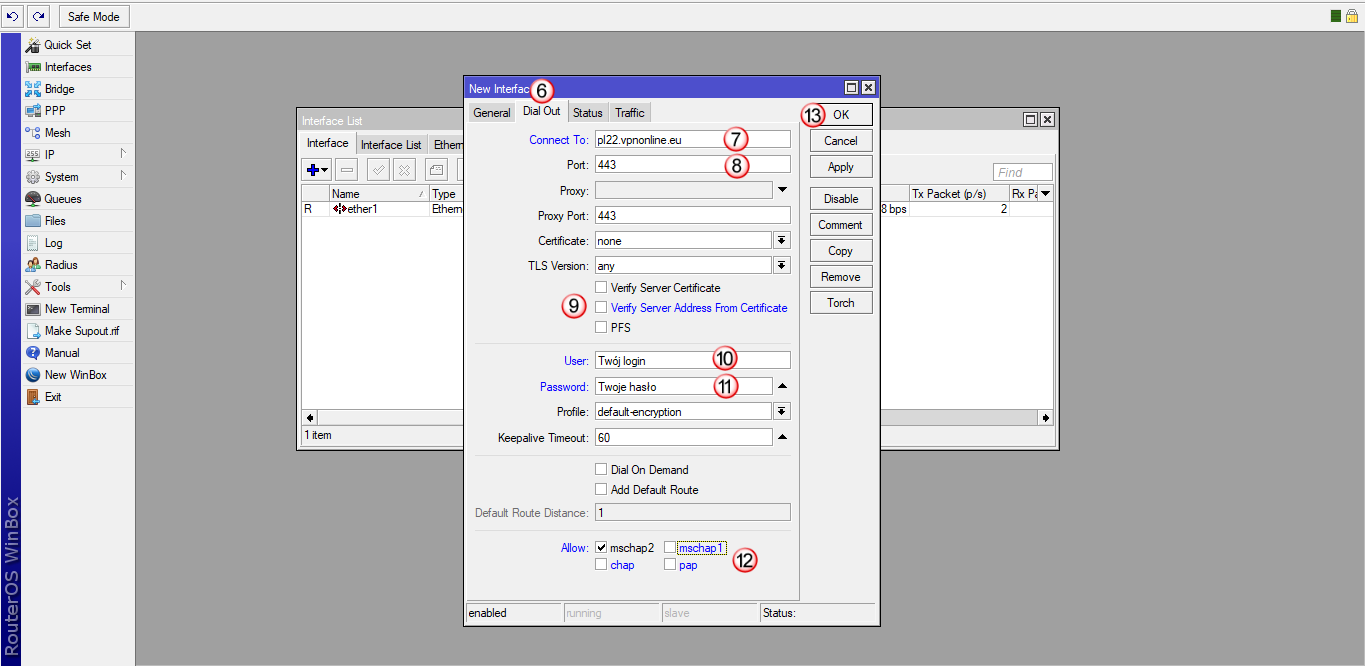
Kliknij zakładkę "IP" (14) i następnie "Firewall" (15)
W oknie "Firewall" wybierz zakładkę "NAT" (16), następnie dodaj nową regułę (17)
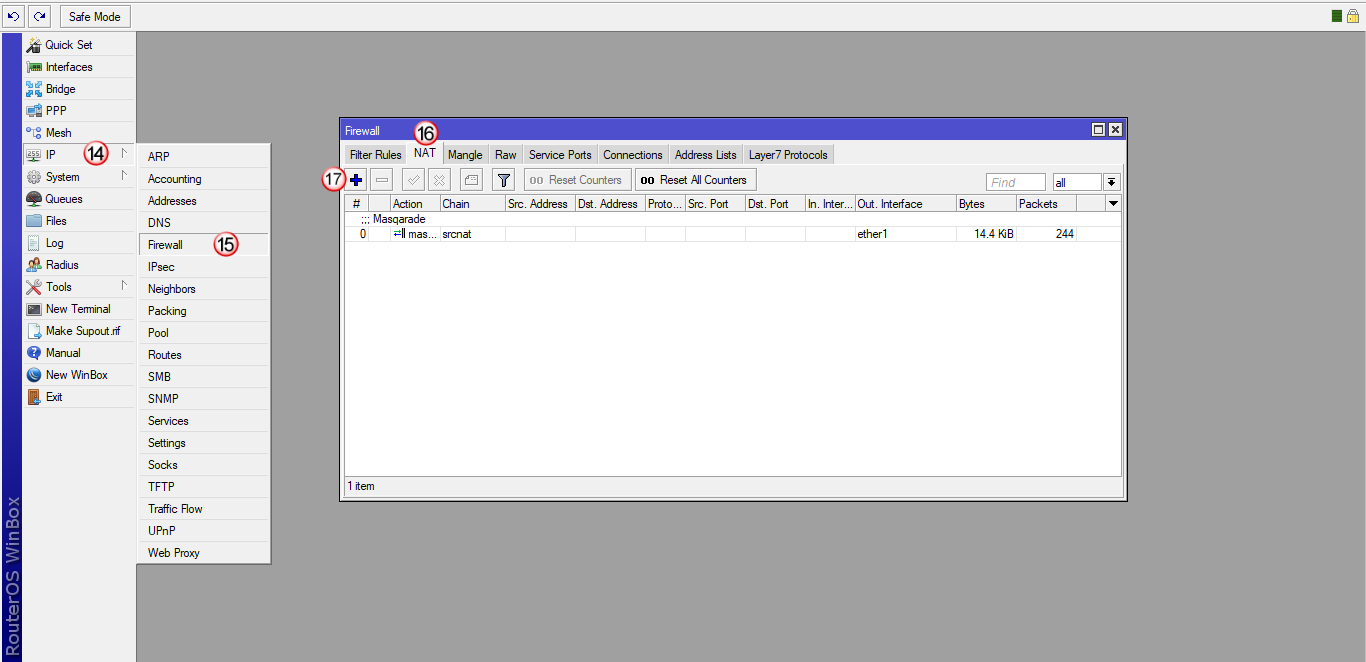
W zakładce "General" (18) wybierz "Chain: srcnat" (19) i następnie "Out. Interface: VPNonline-SSTP" (20)
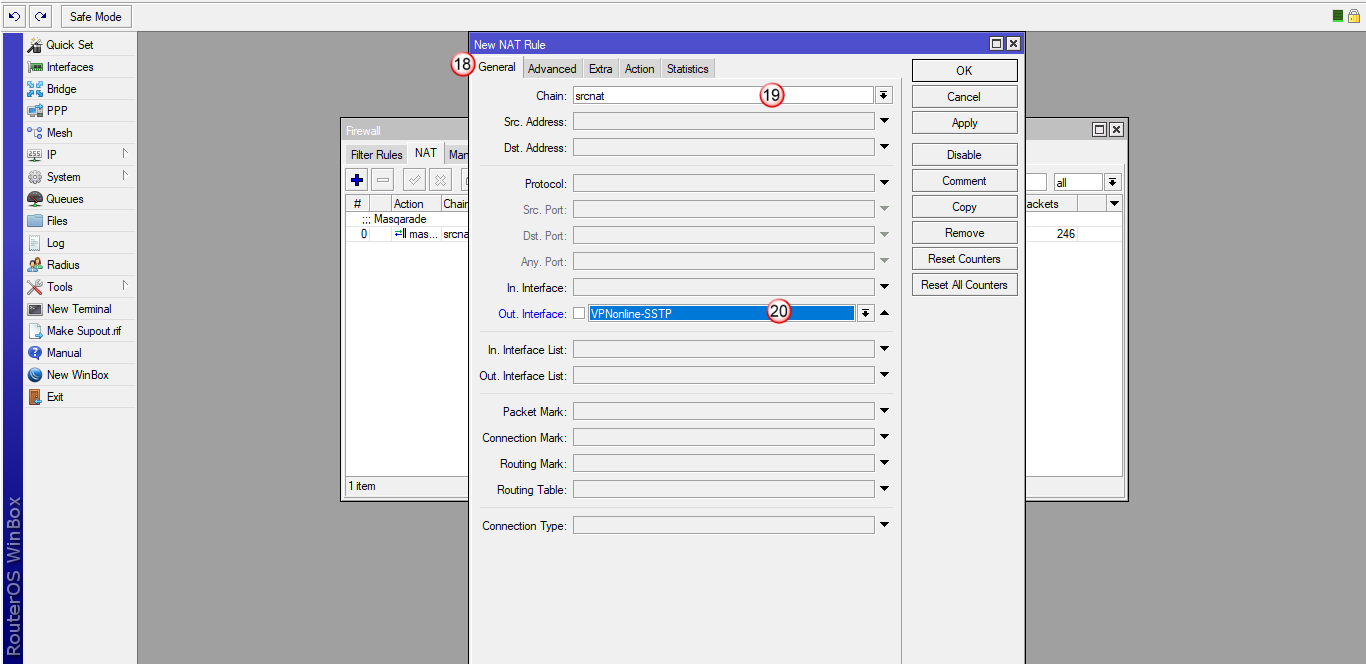
Następnie przejdź do zakładki "Action" (21) i w polu "Action" (22) wybierz "masquerade".
Kliknij "OK" (23)
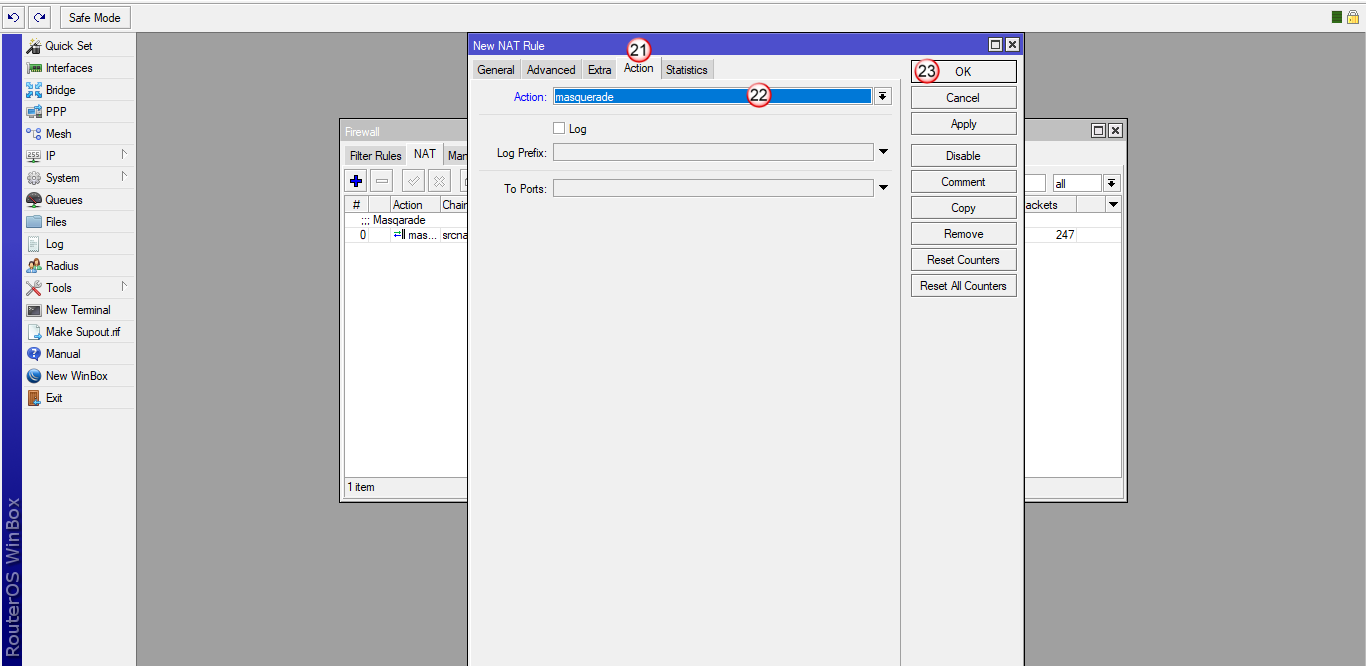
Przejdź do zakładki "Mangle" (24) i dodaj nową regułę (25)
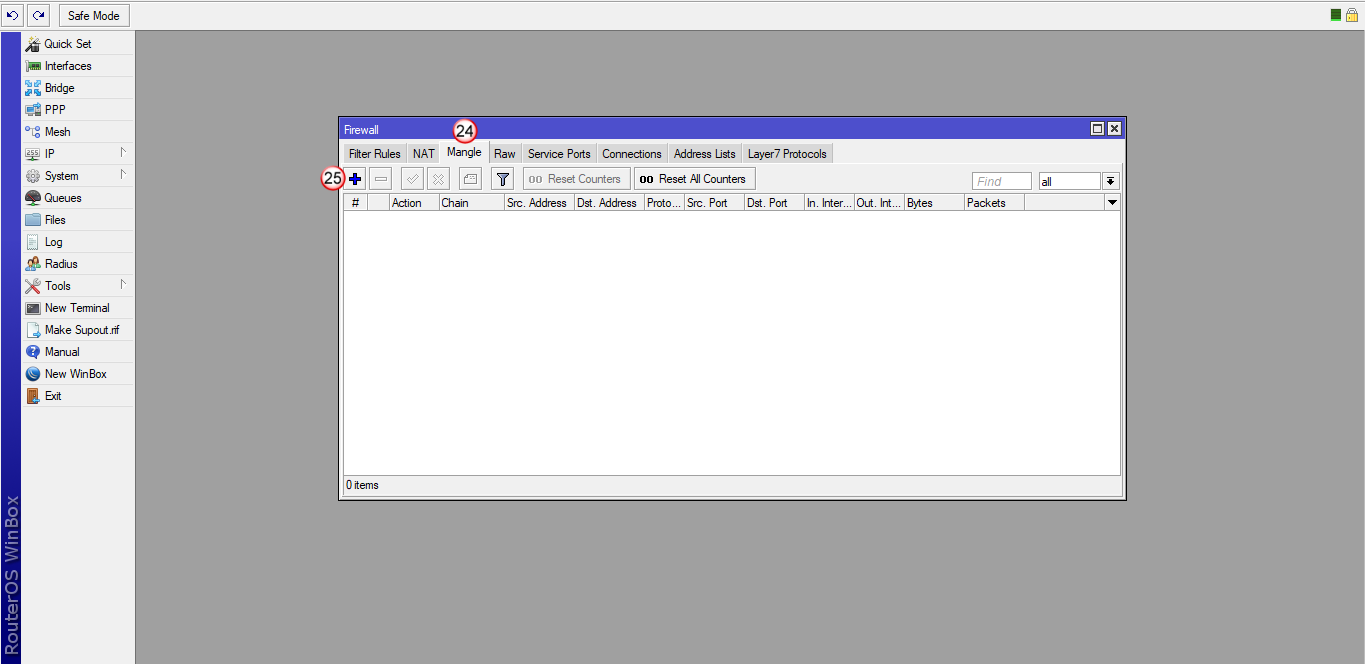
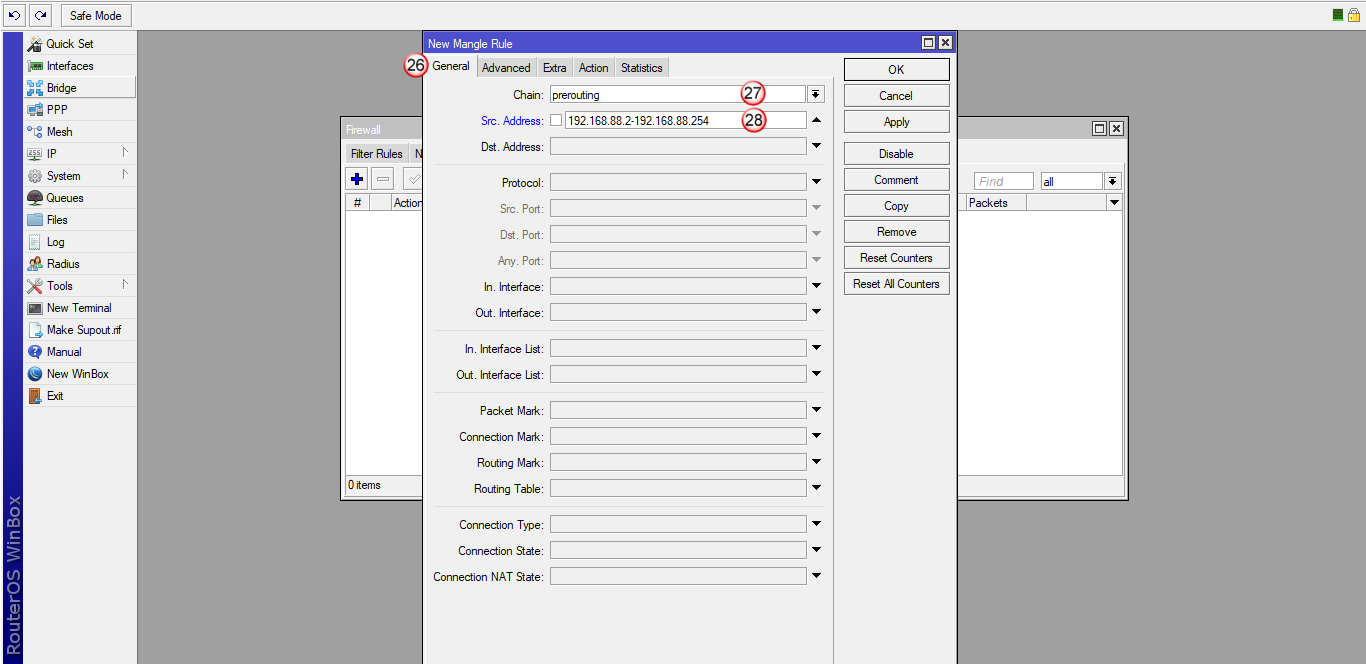
W oknie "New Mangle Rule", wybierz zakładkę "General" (26), następnie wybierz "Chain: prerouting" (27) oraz w polu "Src Address" (28) wpisz adresy IP komputerów, które mają przechodzić przez tunel VPN.
W przykładzie, wpisana jest całą pula adresów IP 192.168.88.2 - 192.168.88.254, ale możesz wpisać tu pojedynczy adres IP hosta np. 192.168.88.10. Dzięki temu, tylko ten host będzie przechodził przez VPN i tylko jego publiczny adres IP zmieni się na adres IP serwera VPN (np. Polski). Pozostałe hosty z puli 192.168.88.0 będą wychodzić przez lokalne łącze do Internetu i będą widoczne w Internecie pod lokalnym publicznym adresem IP.
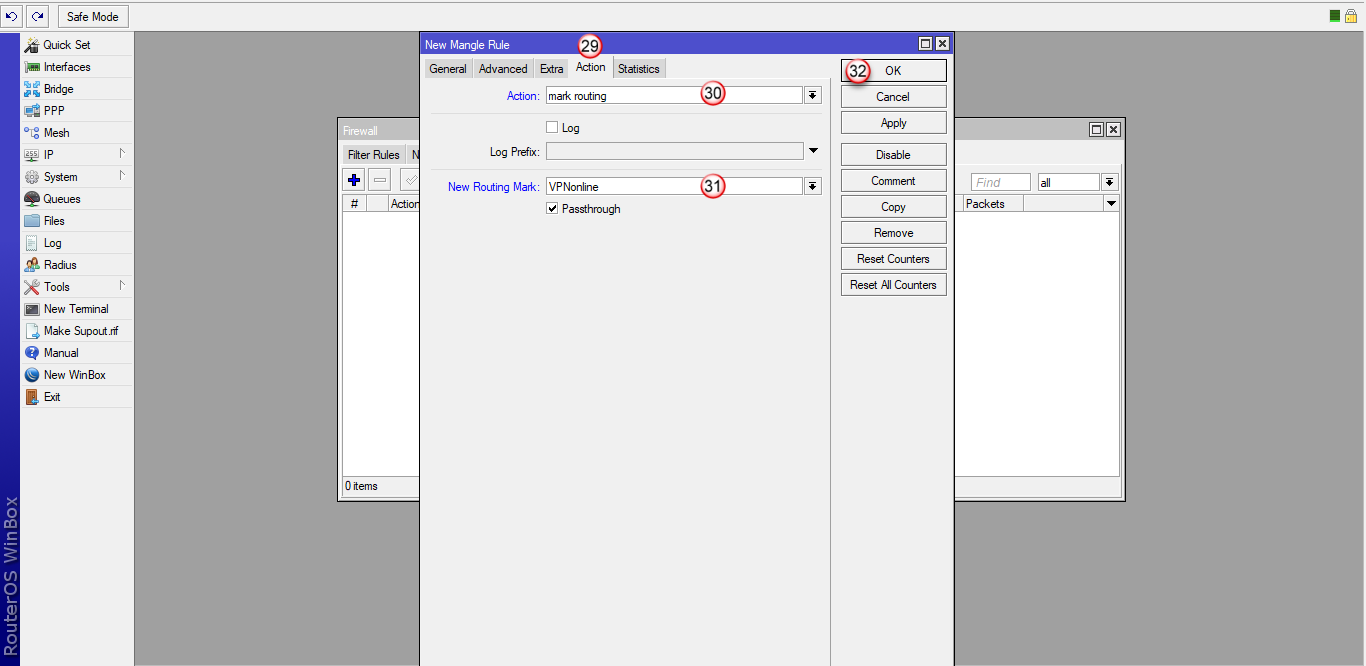
Przejdź do zakładki "Action" (29), w polu "Action" wybierz "mark routing" (30)
W polu "New Routing Mark" (31) wpisz "VPNonline"
Aby zatwierdzić zmiany, kliknij "OK" (32)
Przejdź do zakładki "IP" (33) i "Routes" (34)
W oknie "Route List", w zakładce "Routes" (35), dodaj nową regułę (36)
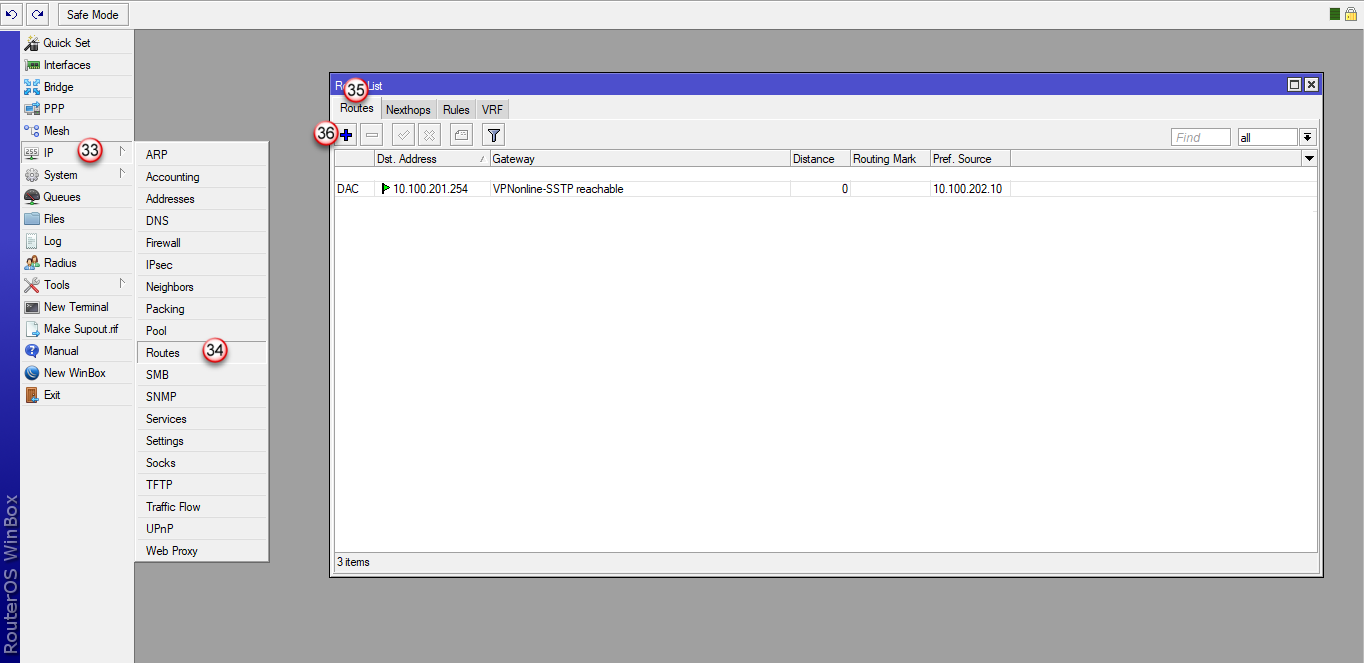
W oknie "New Route", w zakładce "General" (37) wybierz:
"Dst. Address" (38) - 0.0.0.0/0
"Gateway" (39) - VPNonline-SSTP
"Routing Mark" (40) - VPNonline
Aby zatwierdzić zmiany, kliknij "OK" (41)
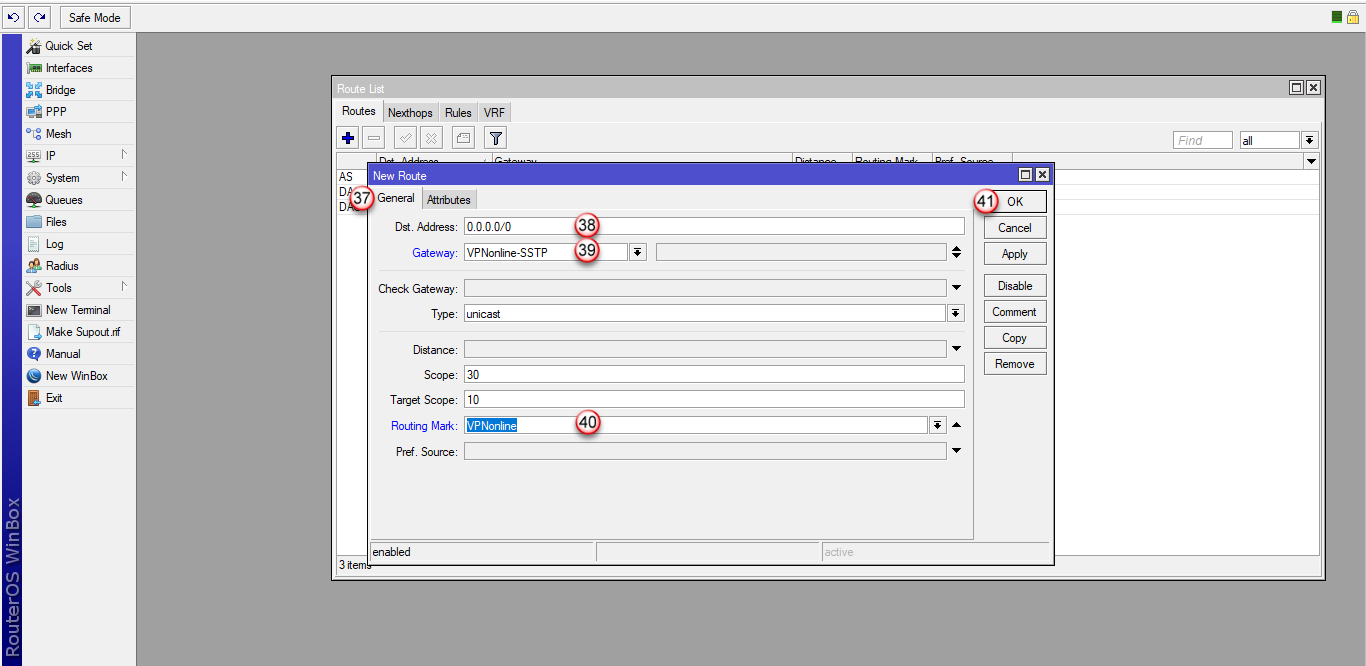
Nowa trasa routingu została dodana (42) i połączenie VPN powinno się zestawić.
Zaloguj się do swojego routera, uruchom przeglądarkę lub skorzystaj z aplikacji WINBOX.
Wpisz domyślny adres routera: http://192.168.88.1
Przejdź do zakładki "PPP" (1) i dodaj (2) nowy interface "OpenVPN Client" (3)
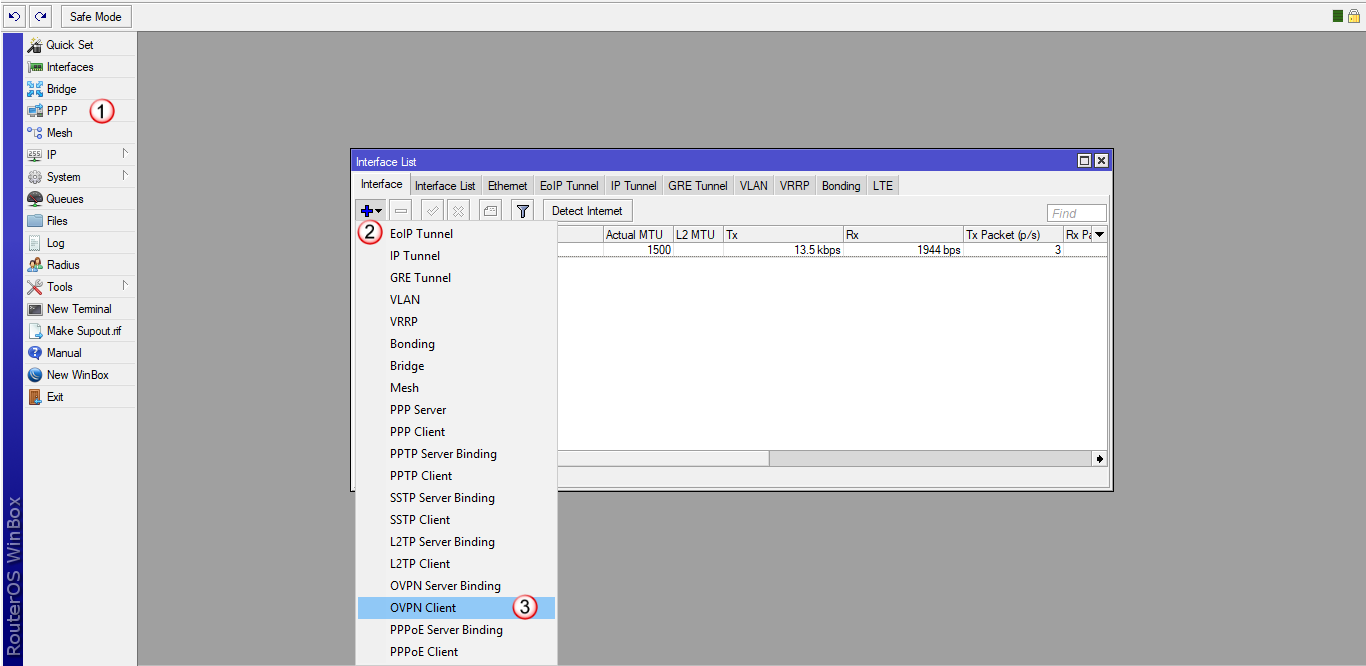
W zakładce "General" (4), w polu "Name" (5) wpisz nazwę interfajsu: VPNonline-OpenVPN
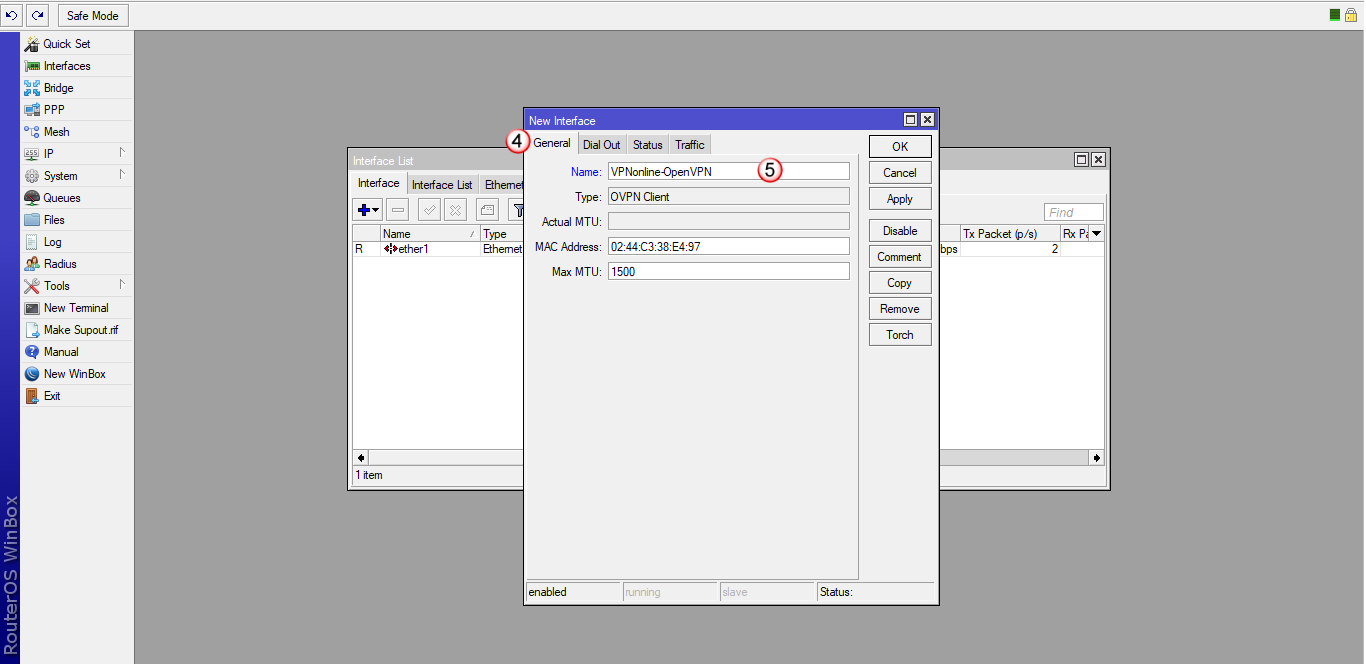
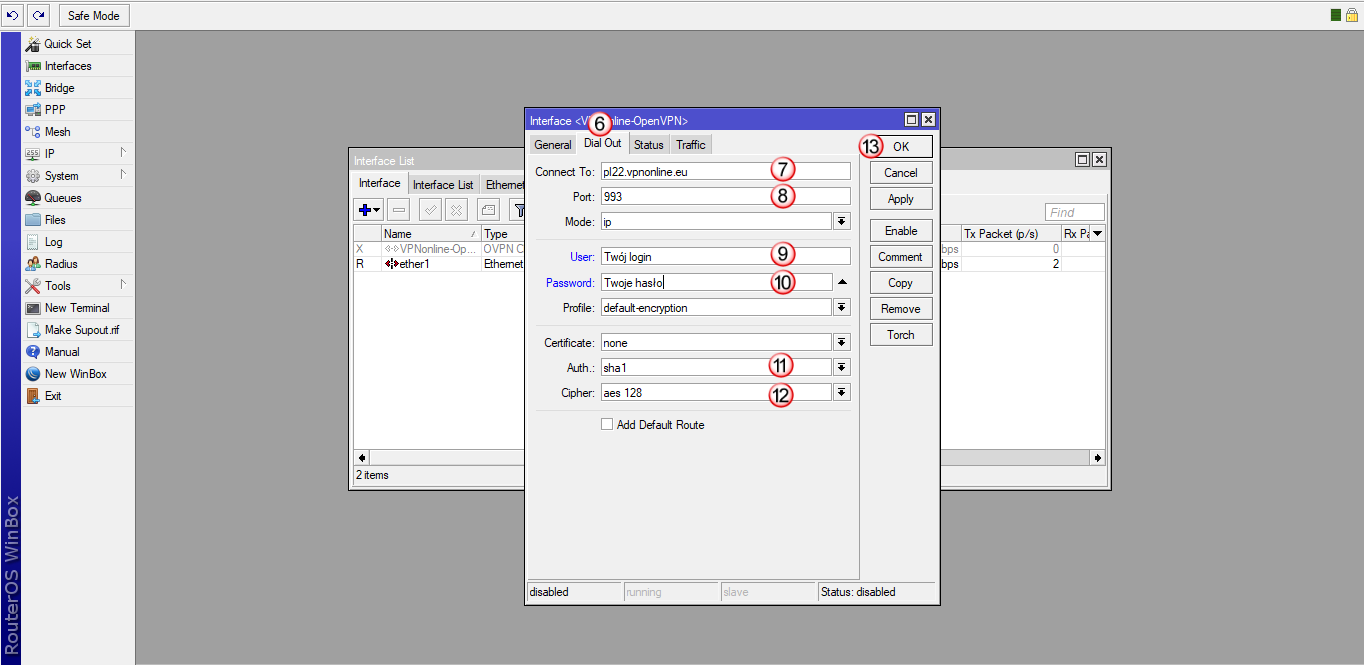
Kliknij zakładkę "Dial Out" (6) i wypełnij poniższe pola:
W polu "Connect to:" (7) wpisz nazwę jednego z naszych serwerów VPN
Listę dostępnych serwerów VPN znajdziesz w panelu klienta: https://portal.vpnonline.pl
W polu "Port:" (8) wpisz: 993 lub 443 w zależności od wybranego serwera VPN
W polu "User:" (9) wpisz swój login
W polu "Password:" (10) wpisz swoje hasło
W polu "Auth:" (11) wybierz: sha1
W polu "Cipher:" (12) wybierz: aes128
Aby zatwierdzić wprowadzone dane, kliknij "OK" (13)
Kliknij zakładkę "IP" (14) i następnie "Firewall" (15)
W oknie "Firewall" wybierz zakładkę "NAT" (16), następnie dodaj nową regułę (17)
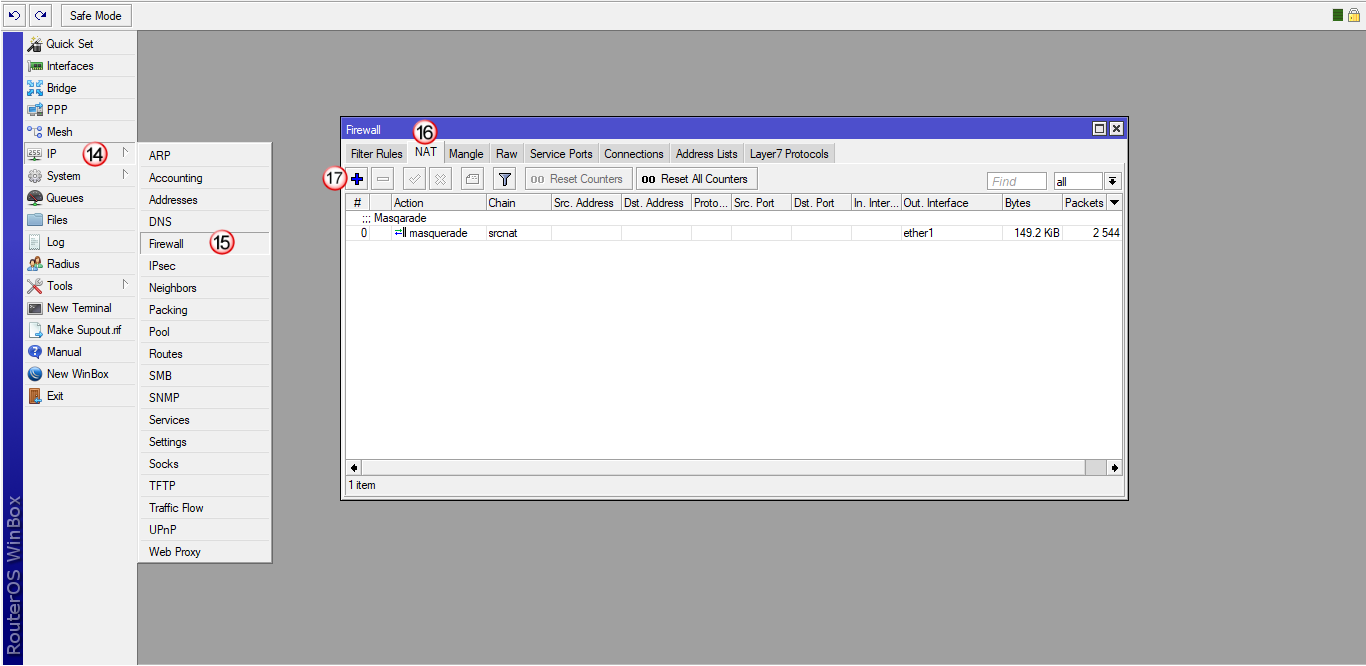
W zakładce "General" (18) wybierz "Chain: srcnat" (19) i następnie "Out. Interface: VPNonline-OpenVPN" (20)
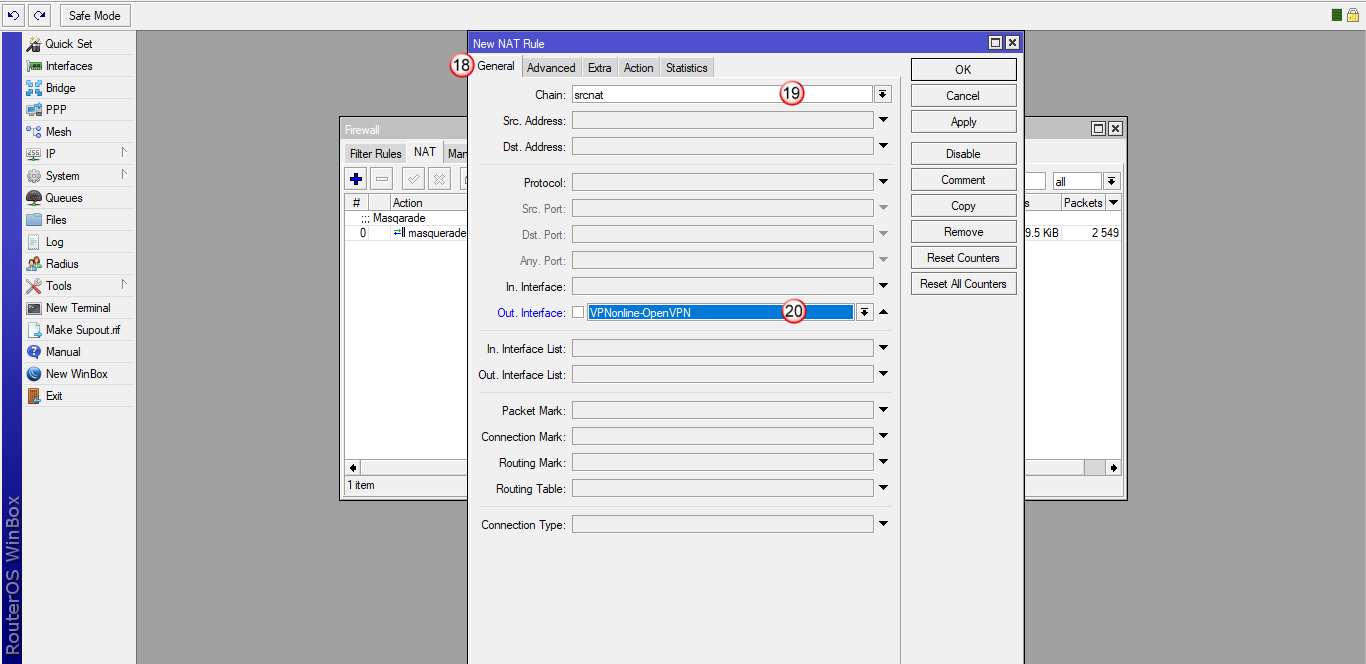
Następnie przejdź do zakładki "Action" (21) i w polu "Action" (22) wybierz "masquerade".
Kliknij "OK" (23)
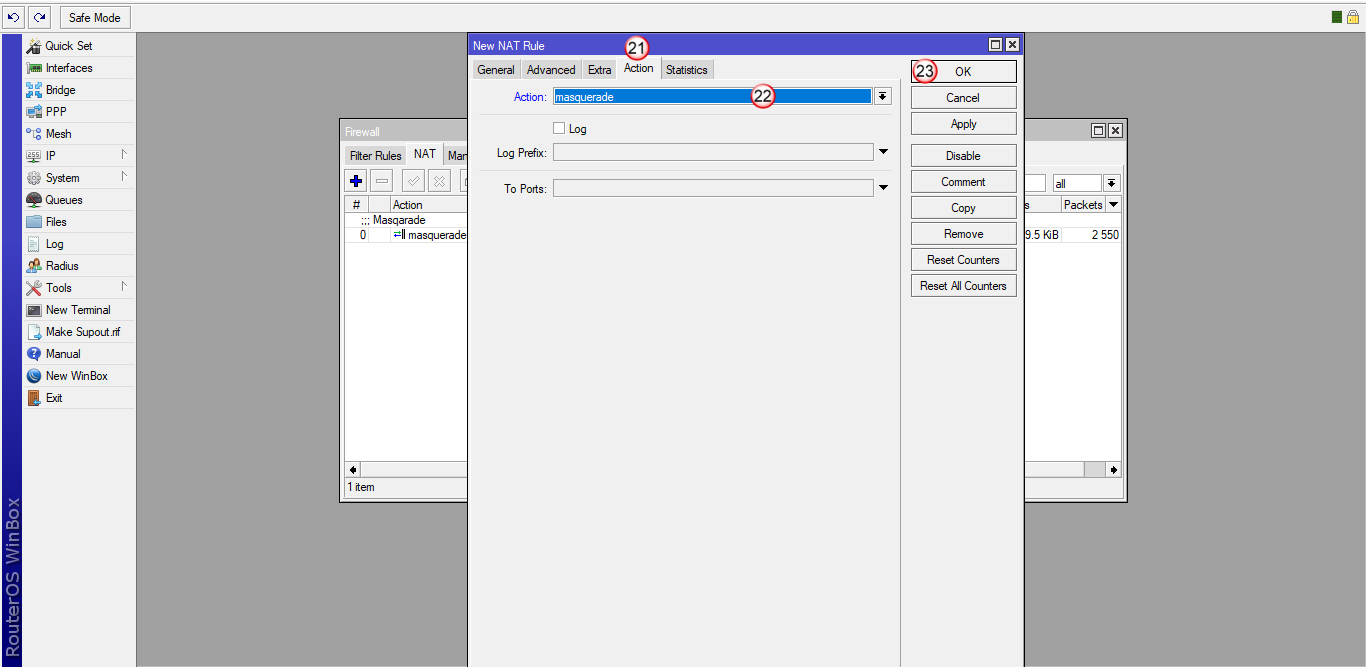
Przejdź do zakładki "Mangle" (24) i dodaj nową regułę (25)
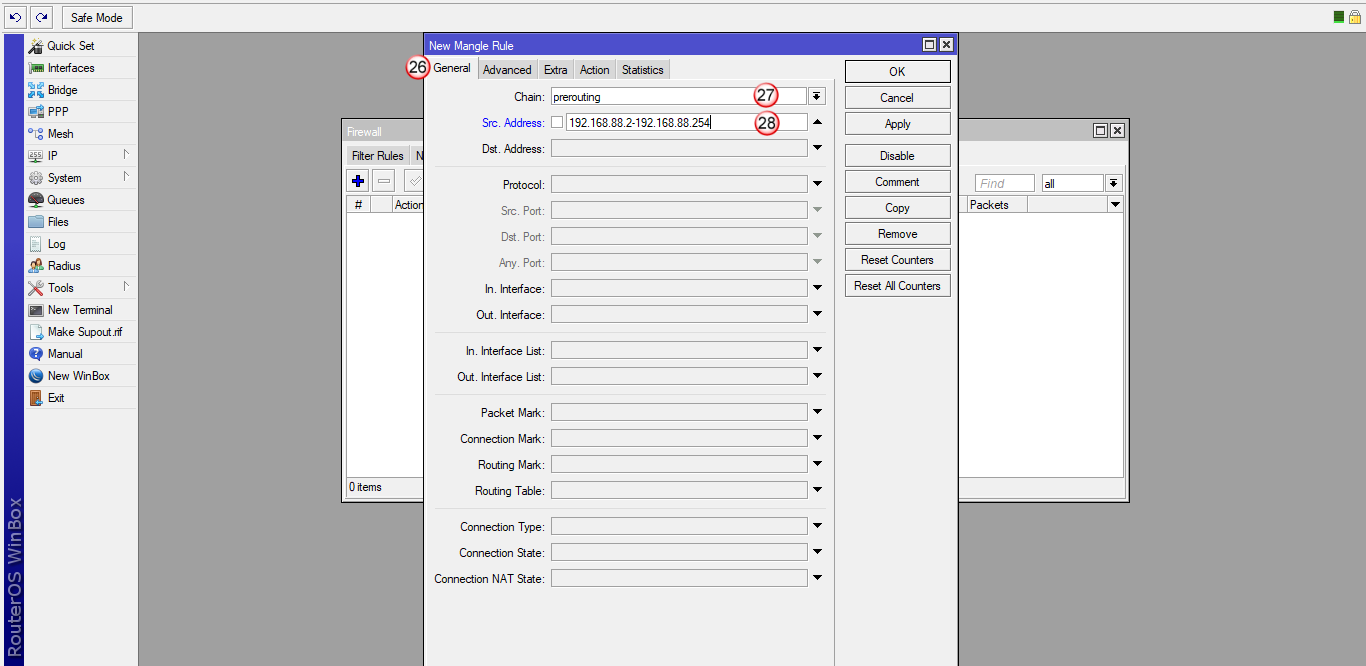
W oknie "New Mangle Rule", wybierz zakładkę "General" (26), następnie wybierz "Chain: prerouting" (27) oraz w polu "Src Address" (28) wpisz adresy IP komputerów, które mają przechodzić przez tunel VPN.
W przykładzie, wpisana jest całą pula adresów IP 192.168.88.2 - 192.168.88.254, ale możesz wpisać tu pojedynczy adres IP hosta np. 192.168.88.10. Dzięki temu, tylko ten host będzie przechodził przez VPN i tylko jego publiczny adres IP zmieni się na adres IP serwera VPN (np. Polski). Pozostałe hosty z puli 192.168.88.0 będą wychodzić przez lokalne łącze do Internetu i będą widoczne w Internecie pod lokalnym publicznym adresem IP.
Przejdź do zakładki "Action" (29), w polu "Action" wybierz "mark routing" (30)
W polu "New Routing Mark" (31) wpisz "VPNonline"
Aby zatwierdzić zmiany, kliknij "OK" (32)
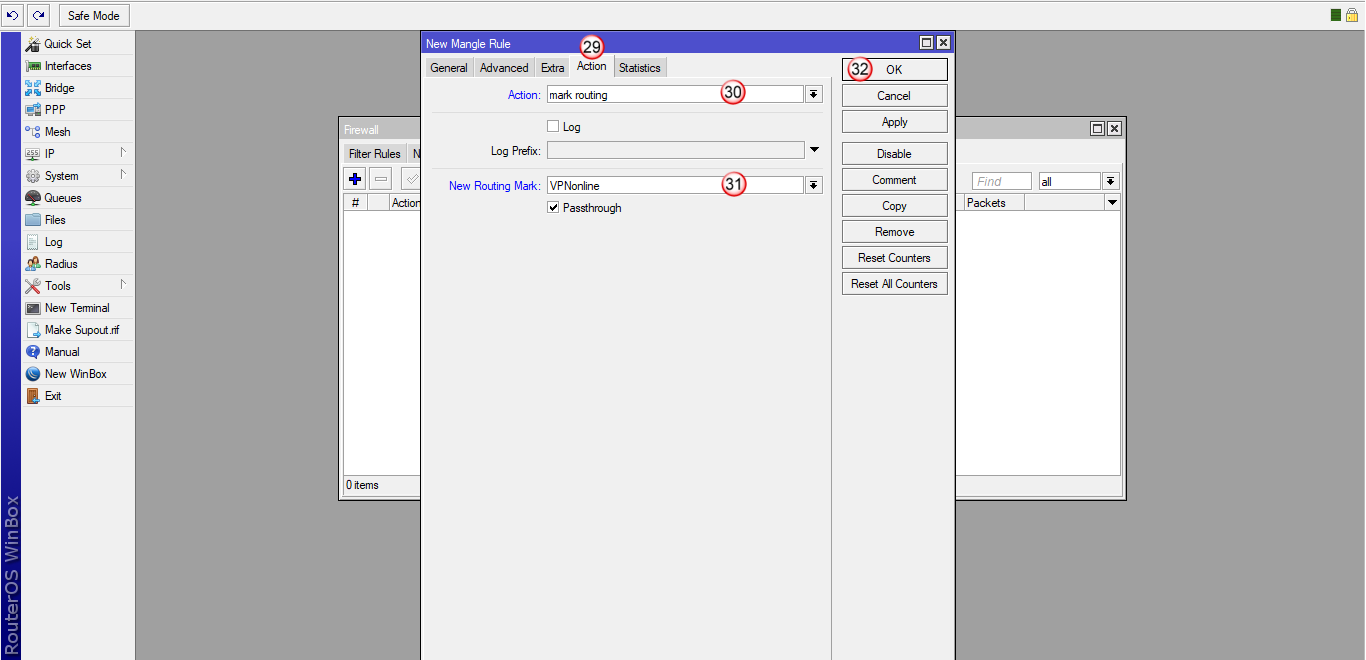
Przejdź do zakładki "IP" (33) i "Routes" (34)
W oknie "Route List", w zakładce "Routes" (35), dodaj nową regułę (36)
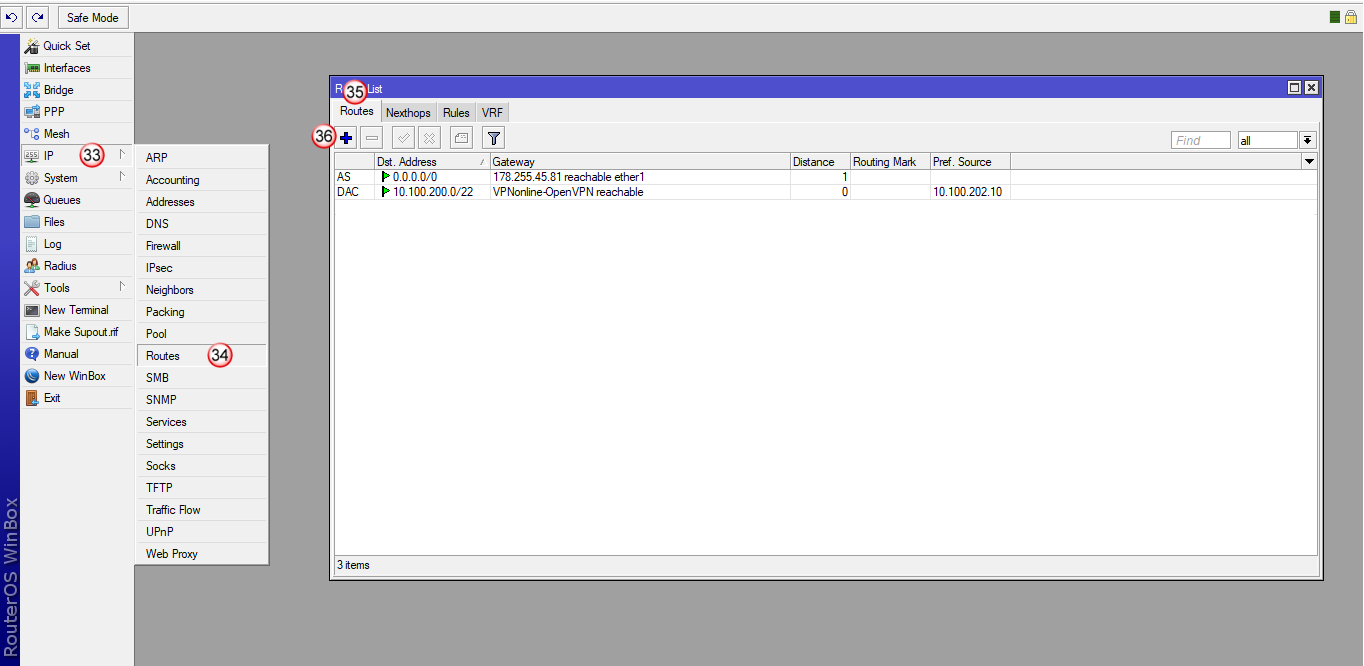
W oknie "New Route", w zakładce "General" (37) wybierz:
"Dst. Address" (38) - 0.0.0.0/0
"Gateway" (39) - VPNonline-OpenVPN
"Routing Mark" (40) - VPNonline
Aby zatwierdzić zmiany, kliknij "OK" (41)
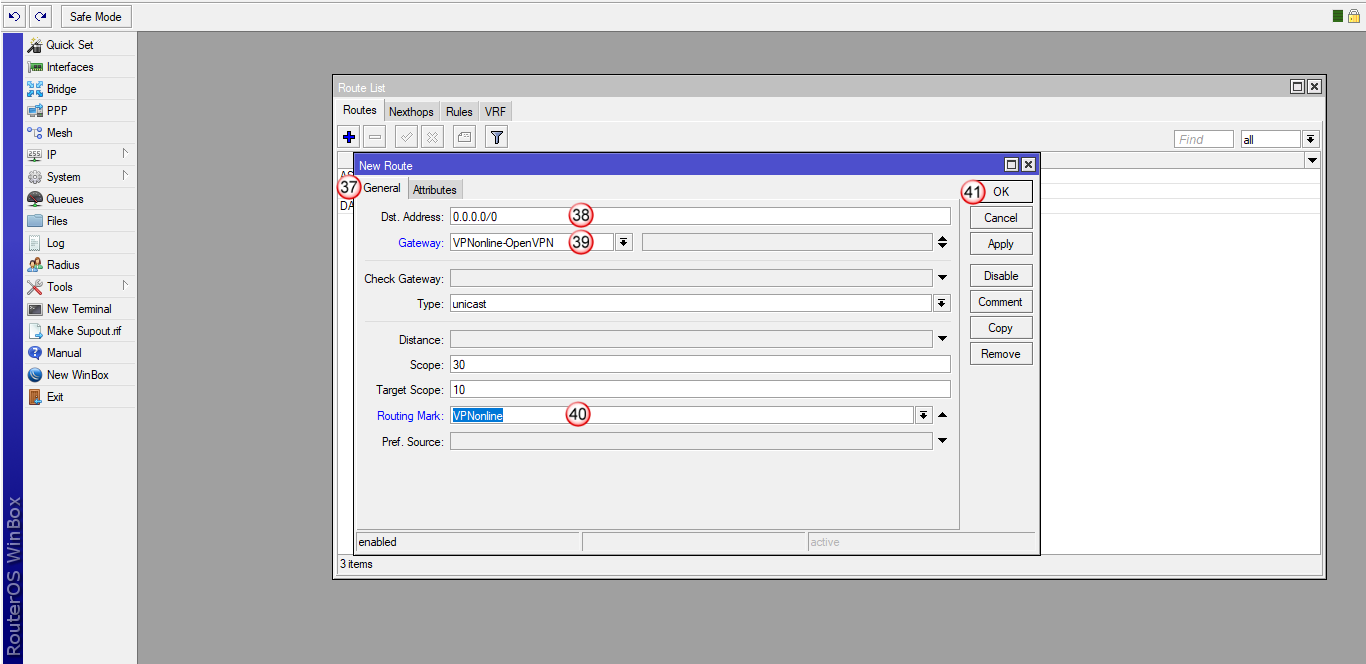
Nowa trasa routingu została dodana (42) i połączenie VPN powinno się zestawić.
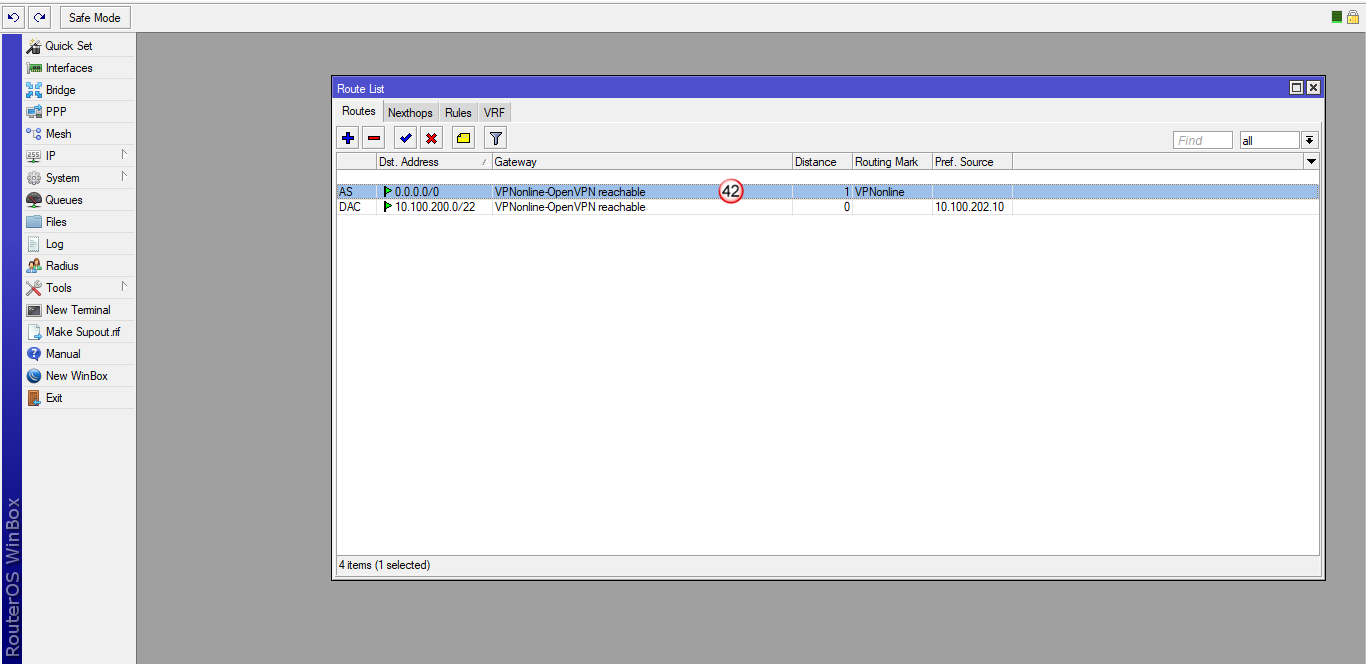
(Stały adres IP zostanie przypisany przez VPNonline na jednym z serwerów VPN
Dostęp do routera, bardzo dobrze się sprawdza na łączach GSM/LTE)
Tylko poniżej zdefiniowane porty bedą przechodzić przez tunel VPN.
Każdy inny ruch do Internetu, będzie wychodził przez lokalne łącze Internetowe.
Winbox - TCP 8291 (port domyślny)
SSH - TCP 22 (port domyślny)
Interface VPN - VPNonline-PPTP ( przykładowy interface VPN)
1. Mangle (Mark Routing) dla wybranej usługi / portu używanego do dostepu (Prerouting oraz Output).
Poniższe wpisy muszą znaleźć się na samej górze reguł Mangle.
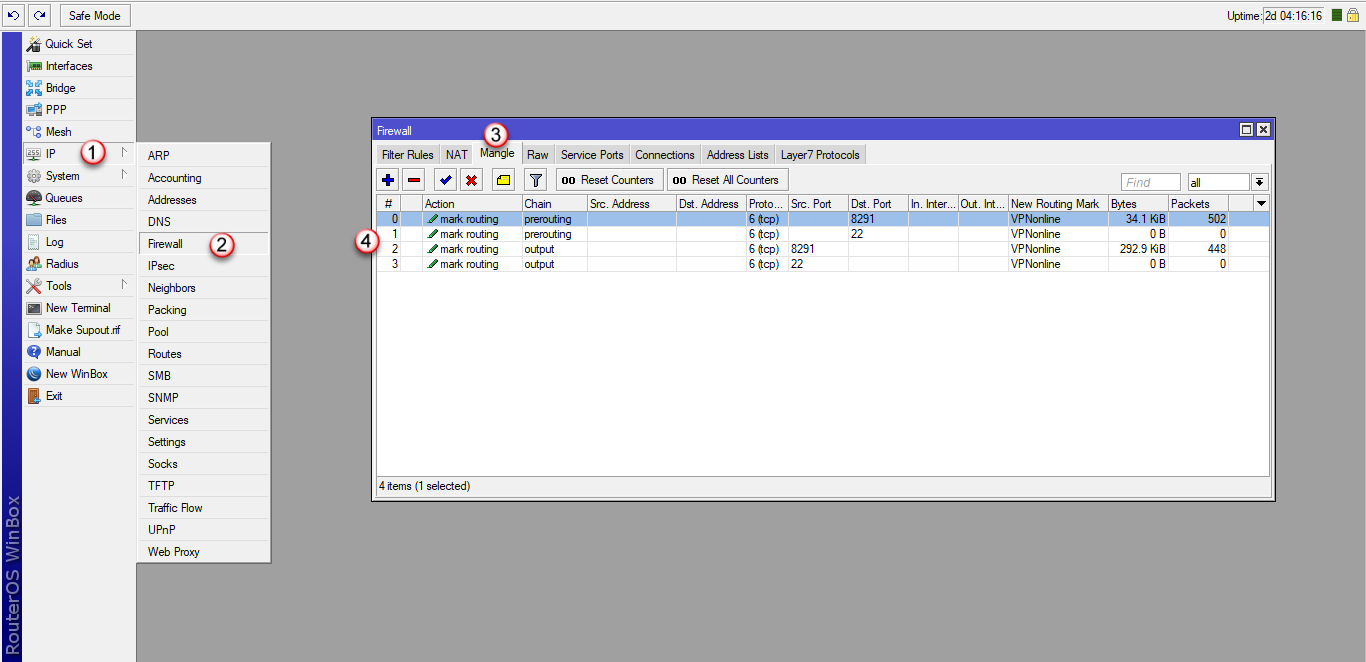
/ip firewall mangle
add chain=prerouting action=mark-routing new-routing-mark=VPNonline passthrough=no protocol=tcp dst-port=8291 log=no log-prefix=""
add chain=prerouting action=mark-routing new-routing-mark=VPNonline passthrough=no protocol=tcp dst-port=22 log=no log-prefix=""
add chain=output action=mark-routing new-routing-mark=VPNonline passthrough=no protocol=tcp src-port=8291 log=no log-prefix=""
add chain=output action=mark-routing new-routing-mark=VPNonline passthrough=no protocol=tcp src-port=22 log=no log-prefix=""
2. Trasa statyczna do Internetu przez interfejs VPN z wybranym Mark Routing
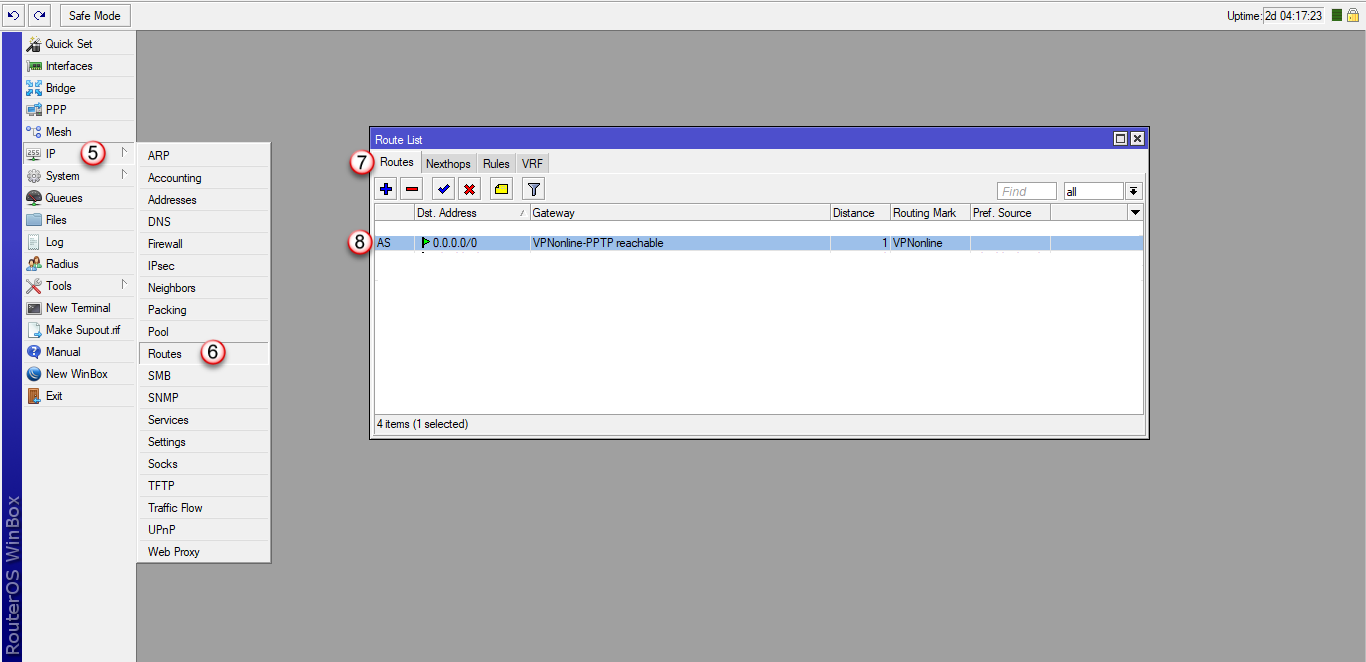
/ip route
add distance=1 gateway=VPNonline-PPTP routing-mark=VPNonline
3. Reguła na Firewallu wpuszczająca ruch do routera z Internetu przez interfejs VPN (VPNonline-PPTP)
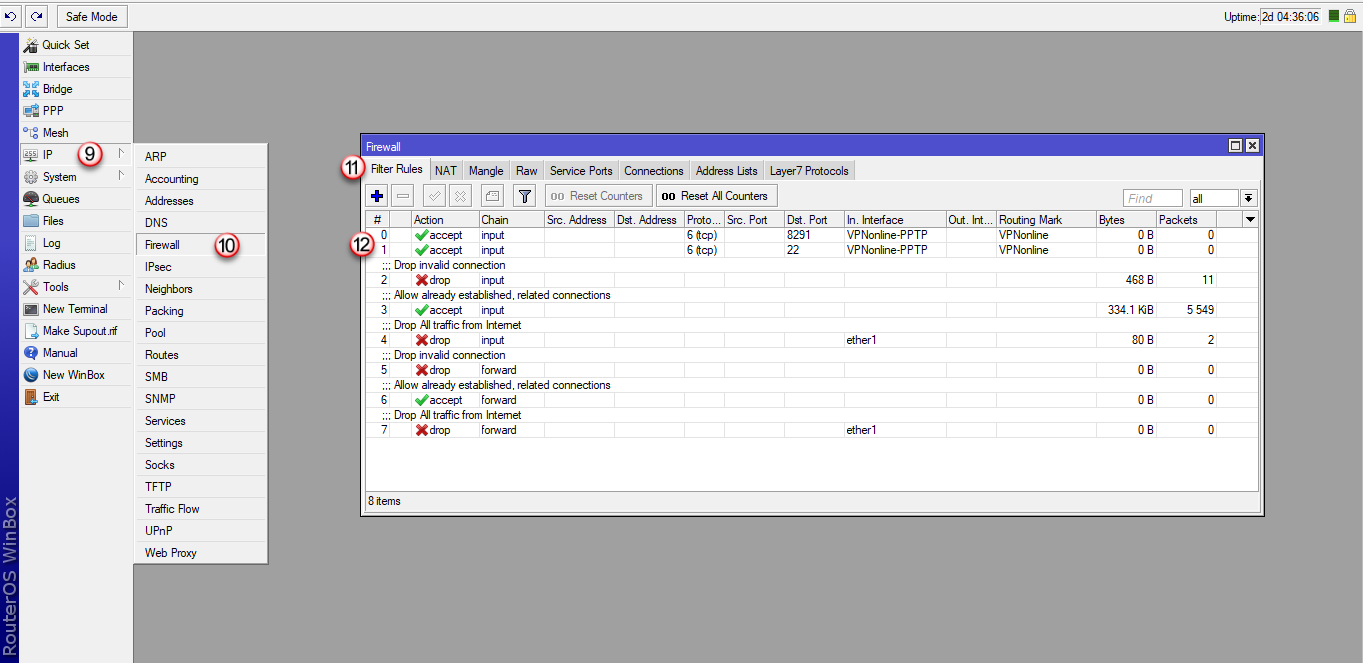
/ip firewall filter
add chain=input action=accept protocol=tcp routing-mark=VPNonline in-interface=VPNonline-PPTP dst-port=8291 log=no log-prefix=""
add chain=input action=accept protocol=tcp routing-mark=VPNonline in-interface=VPNonline-PPTP dst-port=22 log=no log-prefix=""
Tylko poniżej zdefiniowane porty bedą przekierowane z Internetu przez tunel VPN.
Porty do przekierowania - Serwer WWW - TCP 80, 8080 (przykładowe porty)
Adres IP wewnętrzny - Serwer WWW - 192.168.88.200
Interface VPN - VPNonline-PPTP ( przykładowy interface VPN)
1. Przekierowujemy porty w sekcji NAT -DSTNAT oraz dodajemy Masqarade dla ruchu VPN.
Kolejność wierszy ma znaczenie!
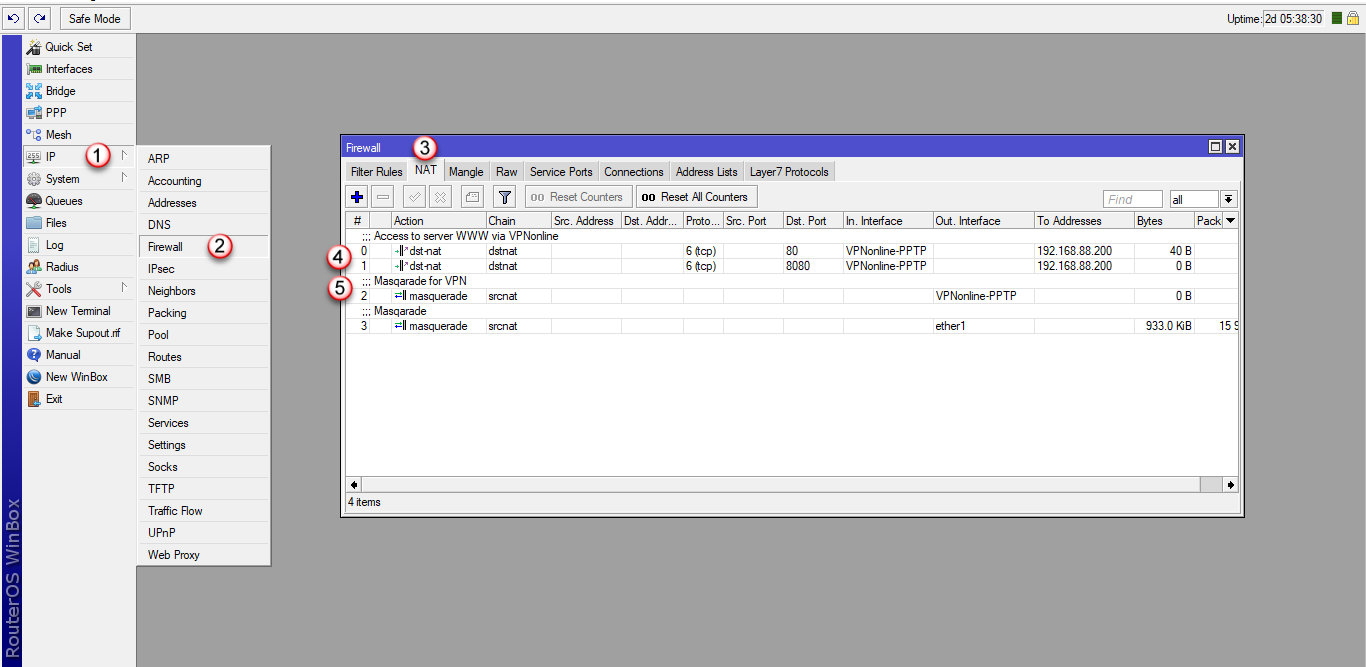
/ip firewall nat
add action=dst-nat chain=dstnat comment="Access to server WWW via VPNonline" dst-port=80 in-interface=VPNonline-PPTP protocol=tcp to-addresses=192.168.88.200 to-ports=80
add action=dst-nat chain=dstnat dst-port=8080 in-interface=VPNonline-PPTP protocol=tcp to-addresses=192.168.88.200 to-ports=8080
add action=masquerade chain=srcnat comment="Masqarade for VPN" out-interface=VPNonline-PPTP
2. Oznaczamy ruch do serwera 192.168.88.200 w sekcji Mangle (New Routing Mark)
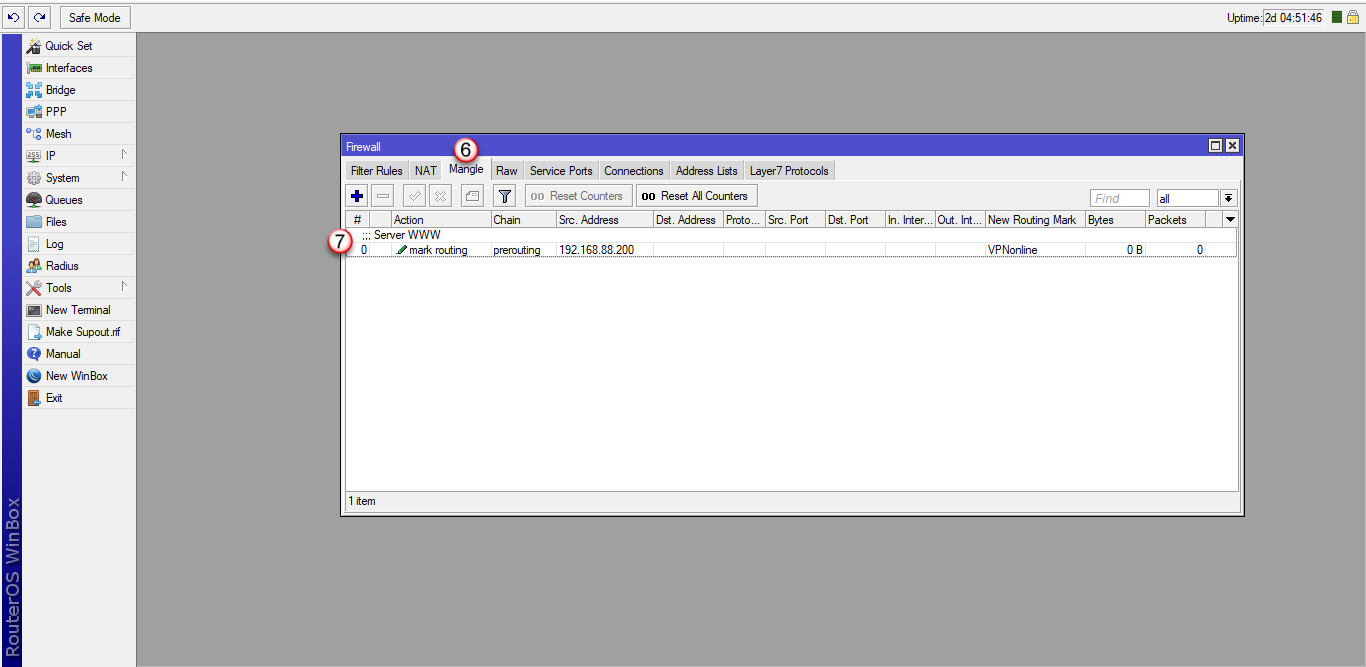
/ip firewall mangle
add action=mark-routing chain=prerouting comment="Server WWW" new-routing-mark=VPNonline passthrough=yes src-address=192.168.88.200
3. Trasa statyczna do Internetu przez interface VPN z wybranym Mark Routingiem
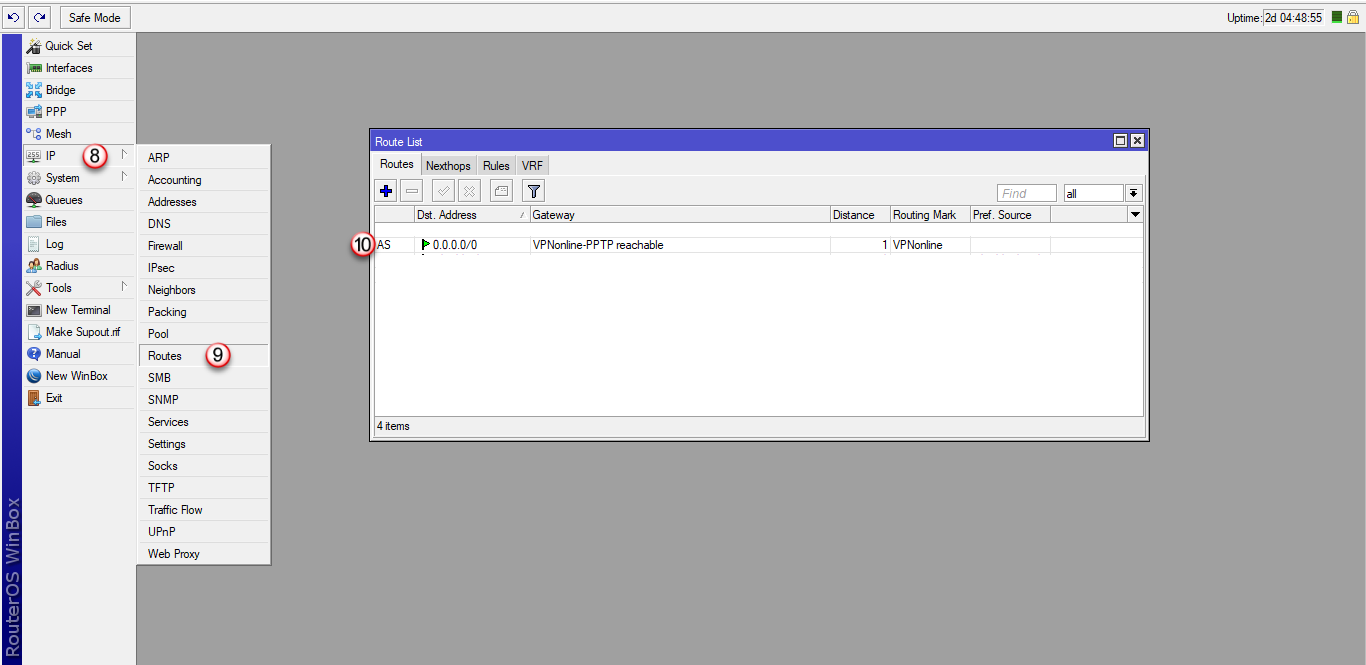
/ip route
add distance=1 gateway=VPNonline-PPTP routing-mark=VPNonline
4. Reguła na Firewallu wpuszcza ruch z Internetu do serwera WWW (192.168.88.200)
Do przekierowania używamy CHAIN FORWARD, kolejność wierszy ma znaczenie!
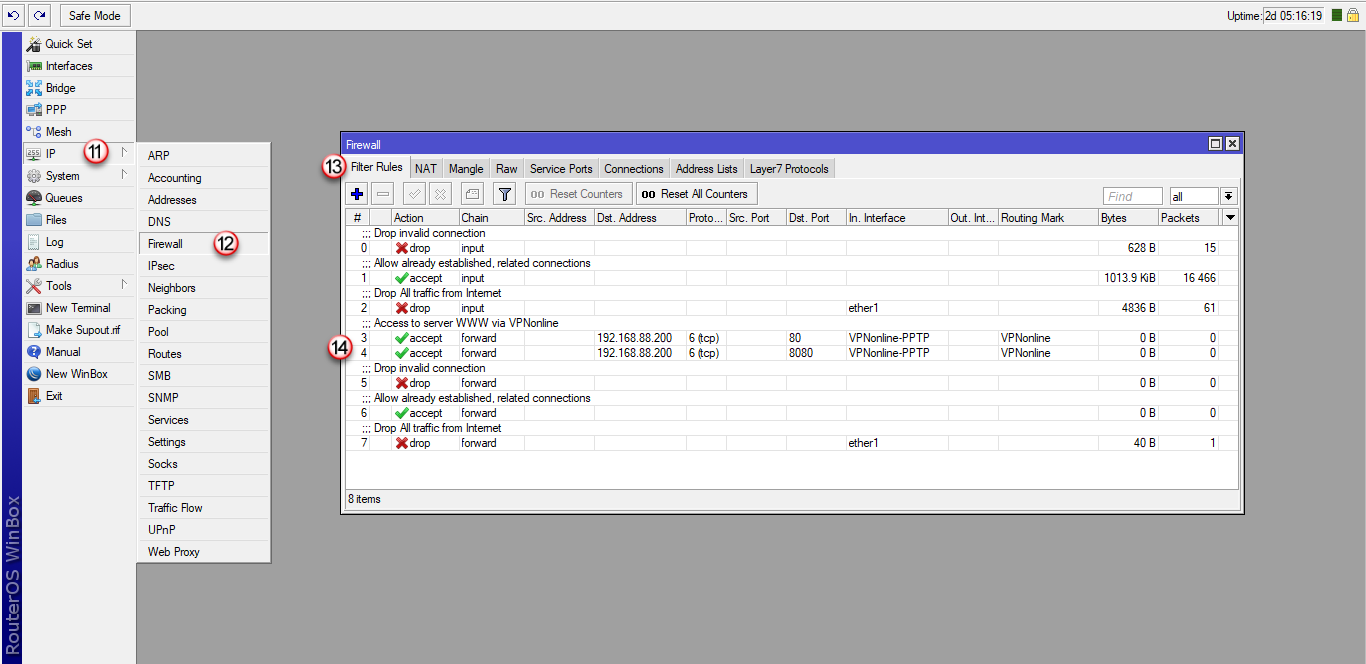
/ip firewall filter
add action=accept chain=forward comment="Access to server WWW via VPNonline" dst-port=80 in-interface=VPNonline-PPTP protocol=tcp routing-mark=VPNonline
add action=accept chain=forward dst-port=8080 in-interface=VPNonline-PPTP protocol=tcp routing-mark=VPNonline